In any complex system, from a factory floor to a bustling city, you need a way to monitor everything to ensure it’s all running smoothly. A modern computer network is no different. With dozens, hundreds, or even thousands of devices working together, how do administrators keep an eye on everything? The answer, for decades, has been a quiet, reliable protocol called SNMP.
In technical terms, SNMP stands for Simple Network Management Protocol. It is a standard internet protocol used for collecting, organizing, and sometimes modifying information about managed devices on IP networks. In essence, it’s the universal language that network devices use to share status updates and health information.
This simple yet powerful system allows network administrators to move from a reactive “firefighting” mode to a proactive management strategy. This guide will break down the core components of SNMP, explain how it works in practice, highlight the crucial differences between its versions, and show you why it remains an absolutely vital tool for anyone managing a network today.
1. The 4 Core Components of SNMP
The SNMP framework is built on four key components that work together in a client-server model. Understanding each part is essential to grasping the entire process. We’ll continue using our inventory system analogy to make each role clear.
The SNMP Manager
The SNMP Manager is the centralized control station of the monitoring system. It’s typically a software platform running on a dedicated server that actively polls devices, receives alerts, and presents the collected data in a human-readable format, like dashboards, graphs, and reports. It is the “brain” of the operation.
The SNMP Agent
The SNMP Agent is a small piece of software that runs on each managed device within the network. This includes your routers, switches, firewalls, servers, and even printers. The agent’s job is to access the device’s local data, retrieve the information requested by the Manager, and send it back. It also has the critical responsibility of sending proactive alerts if something goes wrong.
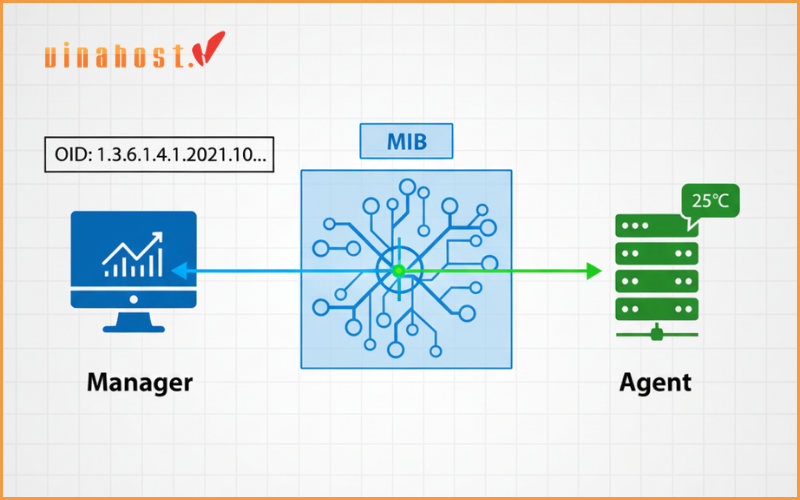
The Management Information Base
A Management Information Base, or MIB, is a structured database of information. It defines, in a hierarchical tree-like structure, every single piece of data that an agent can provide about a device. The MIB acts as a “dictionary” or “codebook” that translates numerical requests from the Manager into understandable data points on the agent. Both the Manager and the Agent must understand the same MIBs to communicate effectively.
The Object Identifier (OID)
The Role: An Object Identifier, or OID, is a unique address that points to a specific piece of information within the vast MIB hierarchy. OIDs are represented as long strings of numbers separated by dots, corresponding to their position in the MIB tree. The Manager uses these OIDs to ask for very specific data.
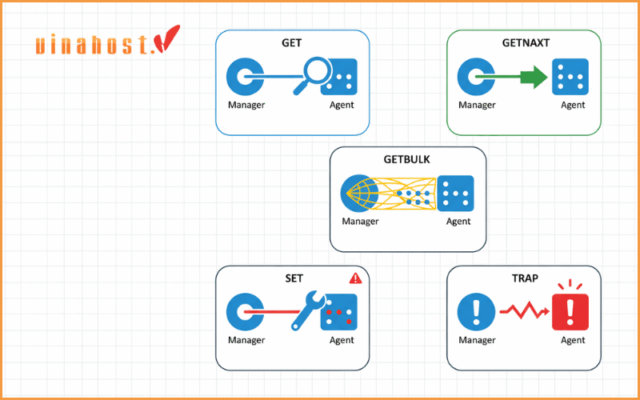
2. SNMP in Action: The Basic Commands
Communication in SNMP is handled by a few simple commands, or Protocol Data Units. These are the core actions that drive all network monitoring activities.
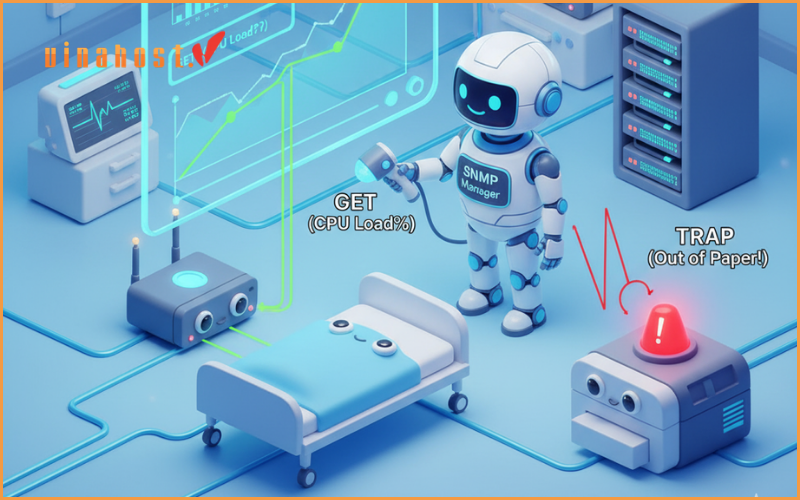
GET: This is the most common command. It is a request sent by the SNMP Manager to an SNMP Agent to retrieve the value of one or more specific OIDs.
GETNEXT: This is a clever command used by managers to “walk” the MIB tree. It asks the agent for the value of the OID that comes after the one specified. By repeatedly using GETNEXT, a manager can discover and retrieve data from an entire section of the MIB without knowing every single OID in advance.
GETBULK: Introduced in SNMP v2c, this is a more efficient version of GETNEXT. It allows a manager to request multiple OID values in a single request, significantly reducing the number of back – and – forth messages and lowering network overhead.
SET: This command is used far less frequently and with extreme caution. It is sent by a Manager to an Agent to change a value on the managed device. This is a powerful command that can be used to reconfigure a device remotely, such as changing its system contact name or shutting down a port. Because of its potential for disruption, its use is often heavily restricted.
TRAP: This is a special, unsolicited message. Unlike the other commands, a TRAP is initiated by the Agent and sent to the Manager to report a significant, pre – defined event. This is the cornerstone of proactive monitoring, as it allows a device to immediately report a problem without waiting for the Manager to ask.
3. The Evolution of Security: SNMP v1 vs v2c vs v3
Like any long – standing internet protocol, SNMP has evolved over the years. The primary driver for these new versions has been the critical need for better security. Understanding the differences is not just academic; it’s essential for maintaining a secure network.
SNMP v1 and SNMP v2c: The Insecure Legacy
SNMP v1: This is the original version, defined in the 1980s. It is foundational but suffers from major security flaws.
SNMP v2c: This version introduced some performance improvements, like the GETBULK command, but it inherited the same flawed security model as v1.
The critical weakness in both v1 and v2c is their authentication method: a simple “community string.” A community string is essentially a plain – text password. The Manager sends a request along with the community string, and if it matches the one configured on the Agent, the Agent responds. This is incredibly insecure because:
The password is sent in plain text over the network. Anyone “listening” to the network traffic can easily capture it.
Once captured, an attacker can use that community string to either query your devices for sensitive information or, if they have the write – access string, use the SET command to maliciously reconfigure your hardware.
For this reason, using SNMP v1 or v2c on any production network today is considered a major security risk.
SNMPv3: The Modern Security Standard
SNMPv3 was designed specifically to address the glaring security holes of its predecessors. It introduced a robust User-based Security Model (USM) that provides a full suite of security features. It is the only version that should be used on modern networks.
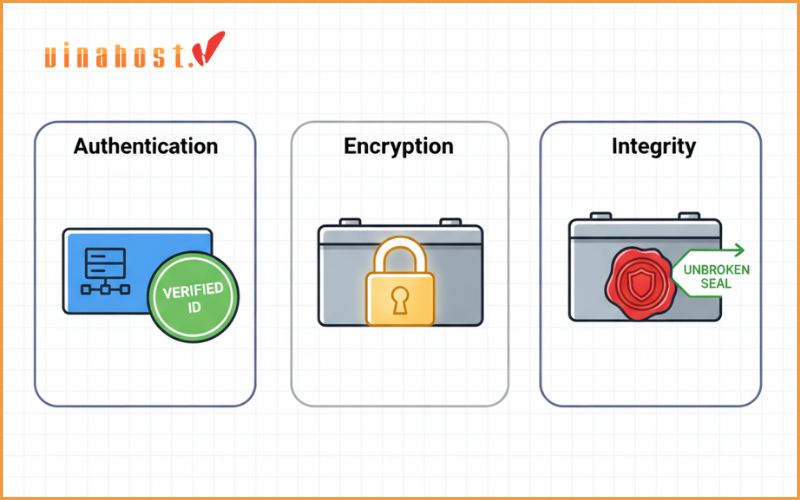
SNMPv3 provides three critical security services:
Authentication: It verifies that a message is actually from a valid and trusted source. Instead of a plain – text community string, it uses hashing algorithms (like MD5 or SHA) to ensure the sender’s identity without exposing a secret password.
Encryption (Privacy): It scrambles the content of the SNMP messages (using encryption standards like DES or AES) while they are in transit. This prevents eavesdroppers from being able to read the data, even if they capture the packets.
Message Integrity: It protects against data tampering. It ensures that the data has not been altered, either accidentally or maliciously, on its way from the Agent to the Manager.
Comparison Table: SNMP Versions
| Feature | SNMPv1 | SNMPv2c | SNMPv3 |
| Authentication | Community String (Plain Text) | Community String (Plain Text) | Username & Hashing (MD5/SHA) |
| Encryption | None | None | Yes (DES, 3DES, AES) |
| Message Integrity | None | None | Yes (via Hashing) |
| Key Commands | GET, SET, TRAP | GET, SET, TRAP, GETBULK | GET, SET, TRAP, GETBULK |
| Security Risk | High | High | Low |
| Recommendation | Do Not Use | Do Not Use | The Only Recommended Version |
4. Common Use Cases: What is SNMP Used For?
Now that we understand the mechanics, where is SNMP actually used in the real world? Its applications are broad and form the bedrock of modern network management.
Performance Monitoring: This is the most common use. Administrators track key performance indicators (KPIs) in real – time and historically. By polling OIDs for bandwidth utilization on router ports, CPU and memory usage on servers, and device temperatures, they can spot performance degradation, identify bottlenecks, and ensure the network is running optimally.
Fault Detection and Alerting: Through the use of SNMP Traps, the monitoring system can become a 24/7 watchdog. An agent can send an immediate alert for critical events like a network link failure, a power supply issue on a switch, a server’s disk running out of space, or a high rate of packet errors on an interface. This allows teams to fix problems before users even notice them.
Network Mapping & Inventory Management: SNMP managers can be configured to scan entire network subnets. By sending GET requests for system description OIDs, they can automatically discover, identify, and map out every SNMP – enabled device on the network. This creates a dynamic, living inventory of all hardware, complete with model numbers, serial numbers, and firmware versions, which is invaluable for asset management.
Capacity Planning: Good network management isn’t just about fixing today’s problems; it’s about preparing for tomorrow’s growth. By collecting and storing SNMP data over weeks, months, or years, administrators can analyze trends. They can accurately predict when a server will run out of memory, when an internet connection will become saturated, or when a switch will run out of available ports, allowing them to justify and plan for upgrades proactively.
SNMP is the silent workhorse that provides the raw data needed to keep our complex, interconnected digital world running smoothly.
 Tiếng Việt
Tiếng Việt English
English 简体中文
简体中文