In our hyper-connected world, from online banking and remote work to streaming services and social media, nearly every aspect of modern life runs on computer networks. But as our reliance on these networks grows, so do the risks. Data breaches, cyberattacks, and system failures are now common headlines, making the practice of securing these digital highways more critical than ever. This is the world of network security.
At its core, network security consists of the policies, practices, and technologies adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and its resources. It’s a broad discipline aimed at protecting the usability, reliability, integrity, and safety of your network and data.
Whether you’re a student, a small business owner, or simply a curious internet user, understanding the fundamentals of network security is no longer optional. This comprehensive guide will explain the core principles that form the bedrock of a strong defense, break down the different types of security tools and controls used to protect a network, and cover the common threats you need to defend against.
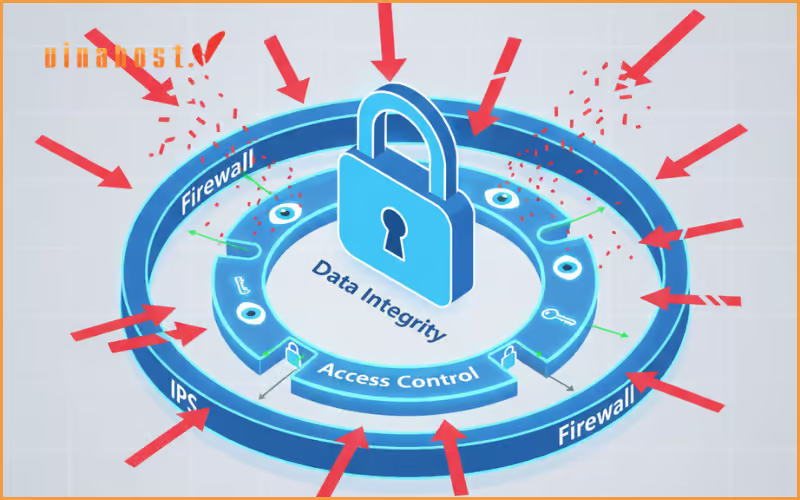
1. The Core Principles: The “CIA Triad” of Network Security
Before diving into the tools and threats, it’s essential to understand the “why” behind network security. The entire field is built on three foundational principles known as the CIA Triad. This isn’t the Central Intelligence Agency, but a model that defines the primary goals for any security program: Confidentiality, Integrity, and Availability.

1.1 Confidentiality
Goal: Ensuring that data is accessible only to authorized users.
Confidentiality is about preventing the unauthorized disclosure of information. It’s the principle that ensures your private data—like bank account details, personal emails, or a company’s trade secrets—remains private. When you see a lock icon in your browser’s address bar, you’re seeing confidentiality in action.
1.2 Integrity
Goal: Maintaining the consistency, accuracy, and trustworthiness of data over its entire lifecycle. In short, preventing unauthorized changes.
Data integrity ensures that the information you are using has not been altered or tampered with. It guarantees that the email you received is the exact one the sender wrote, or that the bank balance displayed on your screen is accurate and hasn’t been maliciously changed. A loss of integrity can be just as damaging as a loss of confidentiality.
1.3 Availability
Goal: Ensuring that the network and its services are available and accessible to authorized users when needed.
Security isn’t just about keeping bad actors out; it’s also about ensuring legitimate users can get in. Availability means that systems, networks, and applications are up and running and that data is accessible when you need it. A Denial-of-Service (DDoS) attack, which floods a website with so much traffic it crashes, is a direct attack on its availability.
2. The Different Types of Network Security Controls
With the “why” established, let’s explore the “how.” Network security controls are the actual tools, technologies, and policies you use to enforce the CIA Triad. Here are some of the most critical types.
2.1 Network Access Control (NAC)
What it is: The “gatekeeper” of your network. NAC is a set of policies and solutions that control who and what devices can connect to your corporate or private network. It’s the first line of defense, determining whether a device is even allowed through the front door.
A robust NAC solution can identify every device on the network and enforce policies based on user role, device type, and even the device’s security posture.

2.2 Firewalls
What they are: A digital barrier that sits between a trusted internal network and an untrusted external network. A firewall inspects all incoming and outgoing traffic and decides whether to allow or block it based on a predefined set of security rules.
Web Application Firewalls (WAF): These are specialized firewalls designed to protect web applications by filtering and monitoring HTTP traffic between a web application and the internet. They can help prevent attacks like SQL injection and cross-site scripting.
2.3 Virtual Private Networks (VPNs)
What they do: Create a secure, encrypted “tunnel” over a public network like the internet. This allows users and devices to connect to a private network remotely as if they were physically present, ensuring that all data transmitted is kept confidential and secure from eavesdroppers.
- Remote Access VPNs: Allow individual employees working from home or on the road to securely connect to their company’s internal network.
- Site-to-Site VPNs: Connect two entire office networks in different locations, creating a single, secure, unified network over the internet.
2.4 Intrusion Prevention Systems (IPS)
What they do: Actively scan network traffic to identify and block malicious activity in real-time. Unlike a firewall, which primarily filters based on rules, an IPS is designed to detect and stop active threats. It acts as a vigilant security guard constantly patrolling the network for suspicious behavior.
An IPS can recognize attack signatures or detect anomalies. When a threat is found, it can automatically block the offending traffic and alert administrators.
2.5 Cloud Security
What it is: A specialized sub-domain of network security focused on protecting data, applications, and infrastructure hosted in a cloud environment (like Amazon Web Services, Microsoft Azure or Google Cloud). As more businesses move their operations to the cloud, securing these virtual networks has become paramount.
Cloud security involves many of the same controls as traditional security – like firewalls and access control – but they are adapted for the dynamic, virtualized nature of the cloud. It also introduces new challenges, such as securing data in a multi – tenant environment and managing the “shared responsibility model” where the cloud provider and the customer share security duties.
2.6 Zero Trust Security
What it is: A modern, strategic security model built on the philosophy of “never trust, always verify”. The traditional “castle-and-moat” approach to security assumed that anything inside the network was trusted. Zero Trust assumes that threats exist both inside and outside the network.
Therefore, no user or device is trusted by default, even if it’s already connected to the corporate network. It requires strict identity

3. Common Network Security Threats
Now that we understand the principles (the why) and the controls (the how), let’s look at the (what). The common threats that these systems are designed to protect against.
3.1 Malware
Malware, short for malicious software, is a catch-all term for any software intentionally designed to cause damage to a computer, server, client, or computer network.
Viruses: Attach themselves to clean files and spread to other clean files, disrupting a system’s functionality.
Worms: Can self-replicate and spread across networks without any human interaction, consuming bandwidth and overloading systems.
Spyware: Secretly records a user’s actions, such as keystrokes or browsing habits, to steal sensitive information.
Ransomware: A particularly nasty form of malware that encrypts a victim’s files. The attacker then demands a ransom from the victim to restore access to the data.
3.2 Phishing
Phishing is a type of social engineering attack where attackers trick users into revealing sensitive information. They send fraudulent emails or create fake websites that appear to be from reputable sources to lure victims into providing login credentials, credit card numbers, or other personal data. It preys on human trust rather than technical vulnerabilities.
3.3 Denial-of-Service (DoS/DDoS) Attacks
A Denial-of-Service (DoS) attack aims to make a machine or network resource unavailable to its intended users by disrupting services. A Distributed Denial-of-Service (DDoS) attack is a DoS attack where the incoming flood of traffic comes from many different sources, making it much more difficult to stop. These attacks violate the “Availability” principle of the CIA Triad by overwhelming a server or network with more traffic than it can handle, causing it to slow down or crash entirely.

3.4 Man-in-the-Middle Attacks
A Man-in-the-Middle attack occurs when an attacker secretly intercepts and relays communication between two parties who believe they are communicating directly with each other. This allows the attacker to eavesdrop on the conversation, steal information, or even inject malicious content into the communication stream. Using an unsecured public Wi-Fi network is a common scenario where users can be vulnerable to MitM attacks.
4. Building Your Defense: A Layered Approach
The key takeaway is that no single security control can protect against all threats. A firewall alone can’t stop a phishing attack, and a VPN won’t protect you from ransomware if you download a malicious file. Effective network security relies on “defense in depth,” a layered security approach where multiple controls are combined.
If one layer fails, another is there to back it up. A strong network security posture combines:
Technical Controls: Firewalls, VPNs, and IPS.
Administrative Controls: Strong security policies, user training, and incident response plans.
Physical Controls: Locks on server room doors and surveillance.
By understanding the principles, implementing the right controls, and staying aware of the threats, you can build a resilient and secure network capable of protecting your most valuable digital assets.
5. VinaHost – Best Dedicated Servers Vietnam: Security You Can Trust
The integrity of your data is paramount, and as you’ve explored the critical aspects of Network Security, it’s clear that your hosting solution must be the strongest line of defense.
A dedicated server offers unmatched control, but true security requires a solid infrastructure and experienced support.
Choosing VinaHost Dedicated Server means you’re not just getting raw power—you’re getting enterprise-grade hardware (Intel Xeon, ECC RAM, Enterprise SSD) deployed in our secure Tier 3 data centers.
This dedicated environment ensures that robust security measures, from advanced firewall configurations to continuous monitoring, are exclusively focused on protecting your applications and data
 Tiếng Việt
Tiếng Việt English
English 简体中文
简体中文