OVERVIEW
Protects your websites and web servers based on the intelligent computing capabilities of Alibaba Cloud Security
Professional, Stable, and End-to-end Solution to the Major Security Pain Points of Web Applications
|  |
| The Only Chinese Vendor That Receives Full Recognition for Web Application Firewalls
|
Multi-scenario Deployment and Flexible Access
|  |
WAF FEATURES

Web Intrusion Prevention
- Automatic Vulnerability Prevention: Automatically detects and defends against the latest web vulnerabilities, including zero-day vulnerabilities first exposed by Alibaba Cloud, within hours. You do not need to manually patch the vulnerabilities.
- Multi-dimensional Dynamic Protection: Provides Alibaba Cloud-developed rules, AI-based deep learning, and proactive protection rules, and dedicated network-wide threat intelligence that is constantly updated to fully protect your services.
- Anti-scanning and Anti-detection: Automatically blocks traffic based on the characteristics and behavior of scanning and detection, network-wide threat intelligence, and deep learning algorithms to prevent attackers from discovering system vulnerabilities.
- Custom Protection Rules: Allows you to create custom protection rules based on your business requirements.
Traffic Control and Bot Management
- Flexible Traffic Management: Supports custom combination of all HTTP headers and body characteristics to implement access control and throttling for specific scenarios.
- Mitigation Against HTTP Flood Attacks: Mitigates HTTP flood attacks by using the default protection policies at different levels, custom protection policies, throttling policies, CAPTCHA verification, and blocking policies.
- Accurate Bot Identification: Accurately identifies bots and automatically responds to bot mutations based on AI technology and multi-dimensional data, such as fingerprints, behavior, characteristics, and intelligence.
- All-scenario Protection: Blocks web bots from accessing applications, such as websites, HTML5 pages, apps, and mini programs. This helps enterprises prevent and control service risks such as fraud and promotion abuse.
- Diversified Methods to Handle Bot Traffic: Provides different methods to handle traffic based on actual scenarios. The methods include blocking, CAPTCHA verification, throttling, and spoofing.
- Scenario-specific Configuration Wizard: Provides guidelines for scenario-specific configurations. This way, new users can quickly get started with Alibaba Cloud best practices.
Data Security Protection
- API Security Protection: Proactively discovers APIs of the earlier versions, APIs that lack the authentication mechanism, and APIs that cause risks such as excessive data exposure and sensitive data leaks.
- Data Leak Prevention: Detects and prevents sensitive data leaks. Sensitive data includes certificate numbers, bank card numbers, mobile phone numbers, and sensitive words.
- Web Tamper Proofing: Locks and caches the content of important pages. This way, users can view the original content of pages regardless of whether the pages are tampered with.
- Account Risk Detection: Automatically identifies common account risks such as dictionary attacks, brute-force attacks, and weak passwords.
Security O&M and Compliance
- Secure Access: Enables you to protect HTTPS services with a few clicks, provides end-to-end IPv6 support, and ensures intelligent load balancing, high availability in and off the cloud, and fast disaster recovery.
- Full Access Logs: Records and stores full web access logs. You can execute SQL statements to query and analyze the logs in real time. You can also create custom alert rules.
- Automatic Asset Identification: Discovers unprotected domain names based on the big data in the cloud. This helps shrink the attack surface.
- Hybrid Cloud Deployment: Provides protection for services that are deployed in data centers.
- Compliance with Classified Protection Requirements: Complies with the requirements of classified protection in various industries.
SCENARIOS
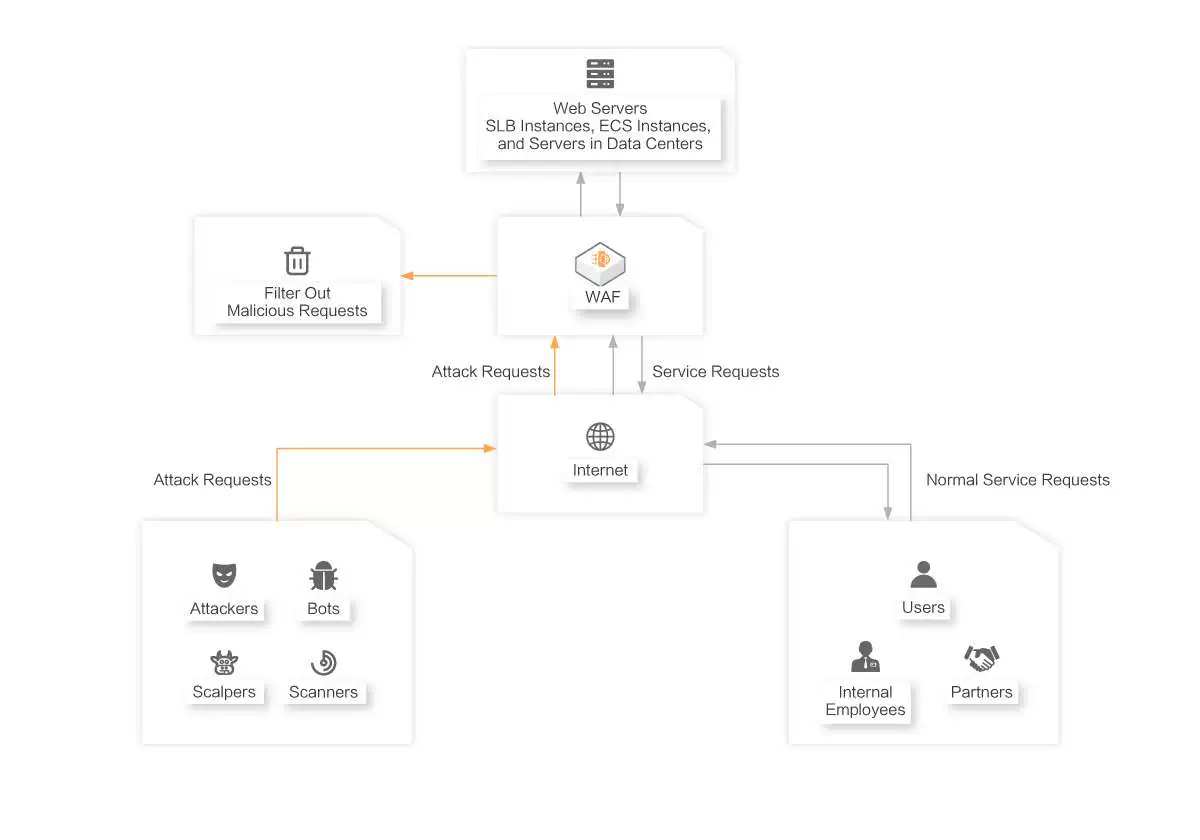 Scenarios of Ensuring Basic Security of Web Applications
Scenarios of Ensuring Basic Security of Web Applications
Security Capabilities Required for Migrating Web Applications to the Cloud
Automatically fixes zero-day vulnerabilities on your web applications. You do not need to manually patch and fix the vulnerabilities. WAF prevents your web applications such as websites, HTML5 pages, apps, and mini programs from being attacked and against virus intrusion in an efficient manner. WAF mitigates attacks such as trojans, web tampering, malicious bots, data leaks, and HTTP flood attacks.
Scenarios
- Prevents common web attacks, such as SQL injections, XSS attacks, webshell uploads, directory traversals, and backdoors.
- Prevents attackers from using zombie servers to launch HTTP flood attacks.
- Automatically fixes zero-day vulnerabilities at the earliest opportunity by using virtual patching. This avoids code rewrite, which is difficult and time-consuming.
- Proactively discovers APIs of the earlier versions, and APIs that lack the authentication mechanism and throttling policies. This helps reduce data leak risks.
- Automatically blocks unauthorized scanning and detection activities.
CONTACT SALES
In 2021, VinaHost Co., Ltd. became an official partner of Alibaba Cloud, providing Cloud Based Services. VinaHost joins Alibaba Cloud Partner Network in order to provide individuals, organizations and businesses with high quality services with higher scalability, resilience, efficiency and innovation.
To buy DCDN, please contact us:
- Hotline: 1900 6046
- Email: support@vinahost.vn
- Livechat: https://livechat.vinahost.vn/chat.php