A proxy server is a crucial component in modern internet usage, serving as an intermediary between a user and the internet. This seemingly simple process offers a myriad of benefits, including enhanced privacy, improved security, and access to restricted content. In this article, VinaHost will explore what is a proxy server, how it operates, and the various types and benefits it provides, offering a comprehensive overview of this essential internet tool.
1. What is a Proxy Server?
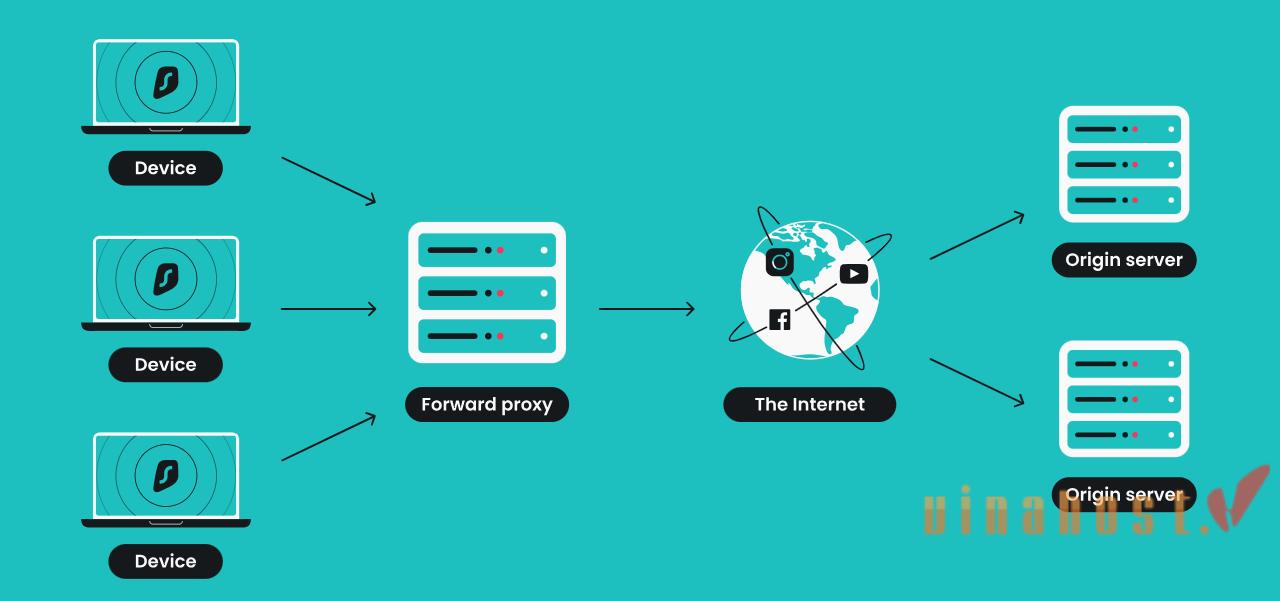
A proxy server acts as an intermediary between a user’s device (such as a computer or smartphone) and the internet. It functions by forwarding client requests to web servers and then sending the server responses back to the clients.
When a user sends a request to access a website or a resource, the request first goes to the proxy server. The proxy server then forwards the request to the target server, receives the response, and sends it back to the user’s device. Proxy servers can provide various benefits, including enhanced security, privacy, access control, and performance optimization through caching.

=> Service Reference: Dedicated Server Cambodia, Proxy Server Thailand, Colocation Vietnam
2. How does a Proxy Server Work?
Now that you understand what is proxy server, let’s delve into an important aspect: how it works.
A proxy server acts as an intermediary between a client device and the internet, receiving requests from the client and forwarding them to the destination server.
When a user wants to access a website, their request is first sent to the proxy server, which evaluates and possibly caches the request. If the content is not cached, the proxy server forwards the request to the destination server, receives the response, and sends it back to the client.
This process can enhance security by hiding the client’s IP address, improve performance through caching, enforce access control policies, filter unwanted content, log user activity, and help bypass geographical restrictions.
To configure a proxy server, users can either purchase or install gateway software on their computer, device, or network. The specific steps for setting up the server will vary based on the operating system and the type of proxy server being used.
Organizations frequently utilize proxy servers to encrypt traffic, preventing third parties from intercepting and reading data as it travels to its destination. Additionally, proxies enable employees to bypass geographical content restrictions and filters that could hinder web scraping activities.
Proxies are also employed to regulate online activities within a workplace. By intercepting and reviewing online requests, a proxy server can block access to certain prohibited websites or IP addresses.
Also read: What is Windows Server? | Features of Windows Server
3. Types of Proxy Servers
3.1. Forward Proxy
A forward proxy acts as an intermediary between a client device and the internet, intercepting requests from the client and forwarding them to web servers. It operates on behalf of the client by caching frequently accessed content to improve performance, filtering web traffic to enforce access policies, and enhancing anonymity by masking the client’s IP address.
Organizations commonly deploy forward proxies in corporate networks to monitor and control internet usage, block access to unauthorized websites, and protect against security threats by inspecting incoming and outgoing traffic.
Additionally, forward proxies are utilized in educational institutions to restrict access to inappropriate content and optimize access to educational resources. They play a crucial role in enhancing network security, optimizing bandwidth usage, and providing a controlled internet environment tailored to organizational policies and user needs.
3.2. Reverse Proxy
A reverse proxy is positioned between the internet and a web server, operating as an intermediary on behalf of the server. It receives requests from clients, forwards them to the appropriate web server, and returns the server’s responses to the clients.
Reverse proxies are essential for tasks such as load balancing, where they distribute incoming traffic across multiple servers to optimize resource utilization and ensure high availability. They also enhance performance through caching, storing frequently requested content to reduce response times.
Moreover, reverse proxies improve security by concealing the identity and internal structure of the web server, thereby safeguarding it from direct exposure to potential threats. This setup is crucial in environments requiring robust security measures and efficient handling of web traffic, such as enterprise applications and high-traffic websites.
3.3. Transparent Proxy
A transparent proxy operates by intercepting requests from clients without requiring any configuration on the client side. It simply passes requests and responses between clients and web servers without altering them. Transparent proxies are commonly employed for tasks like caching frequently accessed content to improve performance and filtering web traffic to enforce access policies.
However, they provide minimal anonymity since they do not mask the client’s IP address, making client identities readily visible to destination servers. This type of proxy is typically used in environments where seamless integration with existing network configurations is prioritized over anonymity, such as in corporate networks and public Wi-Fi hotspots.
Also Read: What is an Application Server? | How Application Server work?
3.4. Anonymous Proxy
An anonymous proxy serves to conceal the client’s IP address from the destination server, offering a layer of privacy and anonymity. It functions by relaying requests between clients and web servers while obscuring the client’s actual IP address.
Although it identifies itself as a proxy to the destination server, it does not disclose the client’s IP address, thus safeguarding the user’s identity from being directly exposed. This type of proxy is valuable for users seeking to browse the internet anonymously, preventing websites from tracking their real IP addresses and location data.
3.5. High Anonymity Proxy
A high anonymity proxy, often referred to as an elite proxy, goes beyond hiding the client’s IP address – it also masquerades as a regular client rather than revealing itself as a proxy server. By not disclosing its proxy nature to the destination server, it enhances anonymity significantly.
This type of proxy offers the utmost level of privacy and security, making it difficult for websites to detect that the requests originate from a proxy server. High anonymity proxies are ideal for users seeking complete anonymity while browsing the internet, as they effectively conceal both the user’s IP address and the fact that a proxy is being used.
3.6. Distorting Proxy
A distorting proxy alters the client’s IP address to a fabricated one while openly identifying itself as a proxy server. This approach offers a degree of anonymity by masking the actual IP address of the client.
However, it explicitly acknowledges the use of a proxy, indicating to the destination server that requests are routed through a proxy server. This type of proxy is useful when users require some level of anonymity while accessing content, but are aware that their activities may be recognized as originating from a proxy server.
Also Read: What is a Cloud Server? | How does a Cloud Server work?
3.7. Data Center Proxy
A data center proxy operates independently of an Internet Service Provider (ISP) and is hosted within a data center environment. These proxies are known for their speed and scalability, making them suitable for various online activities.
However, they are easily recognizable as proxies because they utilize IP addresses from well-known data center ranges. This characteristic can sometimes lead to restrictions or blocks from websites that aim to differentiate between legitimate user traffic and proxy server requests.
Despite this, data center proxies remain popular for their reliability and performance in scenarios where speed and scalability are paramount considerations.
Read more: Vietnam Dedicated Server
3.8. Residential Proxy
A residential proxy utilizes an IP address issued by an Internet Service Provider (ISP), giving the impression that the internet traffic originates from a residential user.
This type of proxy is designed to mimic the behavior of genuine residential users, making it more challenging to identify and block compared to data center proxies.
Websites and online services often find it difficult to distinguish between legitimate residential users and residential proxies, enhancing their effectiveness for activities such as web scraping and bypassing geo-restrictions. Residential proxies are valued for their ability to provide authentic-looking traffic while offering a higher level of anonymity and reliability in comparison to other proxy types.
3.9. Public Proxy
A public proxy is accessible to anyone without restrictions on usage. These proxies are typically available for free and are utilized by users seeking to mask their IP addresses or bypass geographical restrictions.
However, public proxies often suffer from reliability issues due to high traffic volume, leading to slower connection speeds and frequent downtime.
Moreover, they pose security risks because they may not be adequately maintained or could be operated maliciously to intercept users’ data. As a result, while public proxies offer a cost-free option for accessing blocked content or enhancing privacy, users should exercise caution and consider the potential security implications when utilizing them.
Also Read: What is a Thailand Server? Top 5 choosing the right Thailand Server Provider
3.10. SSL Proxy
An SSL proxy, also known as a Secure Sockets Layer proxy, employs SSL encryption to secure data transmitted between a client and the proxy server.
This encryption ensures that sensitive information remains protected during transmission, safeguarding against interception or tampering by unauthorized parties. SSL proxies are instrumental in providing secure communication channels and enabling users to access websites securely, particularly when handling confidential data such as login credentials or financial information.
By encrypting data in transit, SSL proxies enhance overall security and privacy for users engaging in online activities that require heightened protection against potential cyber threats.
3.11. Shared Proxy
A shared proxy is a type of proxy server that is accessed and used concurrently by multiple users. This shared usage model can be cost-effective since the cost of maintaining the proxy server is distributed among multiple users.
However, shared proxies often result in slower connection speeds and increased risks of being blocked or blacklisted by websites. This is because the actions of one user, such as engaging in suspicious or prohibited activities, can affect the reputation of the shared IP address. Consequently, websites may impose restrictions or bans on shared proxy IPs to mitigate potential risks.
Despite these drawbacks, shared proxies remain popular among users seeking affordable proxy solutions for various online activities, including web scraping, anonymity, and accessing geo-restricted content.
3.12. Rotating Proxy
A rotating proxy automatically switches the IP address assigned to the client at predefined intervals or after each request. This dynamic IP rotation strategy helps to evade IP bans and circumvent rate limits imposed by websites or online services. Rotating proxies are particularly valuable for tasks like web scraping, where accessing data from multiple sources or avoiding detection is essential.
By frequently changing IP addresses, rotating proxies enhance anonymity and reliability in automated processes, ensuring uninterrupted access to online content while mitigating the risk of being blocked or flagged for suspicious activity. This makes them a preferred choice for users engaging in activities that require frequent IP address changes to maintain operational continuity and evade restrictions.
Also read: What is Minecraft Server? | Everything you need to know
4. Benefits of Using a Proxy Server
Proxy servers provide a versatile solution for enhancing security, privacy, and efficiency in both personal and organizational internet usage:
- Enhanced privacy: By hiding your IP address from websites you visit, proxy servers can offer a layer of anonymity online. This makes it more difficult for websites and online trackers to monitor your browsing activity and collect your data.
- Improved security: Some proxy servers can act as a security barrier, filtering out malicious content or websites known for phishing attacks. This can help to protect you from malware and other online threats.
- Content access: Proxy servers can be used to bypass geo-restrictions. If a website is blocked in your region, you can potentially access it by routing your traffic through a proxy server located in a different country.
- Faster performance: In some cases, proxy servers can improve website loading times by caching frequently accessed data. This means the content is stored locally on the proxy server, so it can be retrieved more quickly the next time you need it.
- Content filtering: Organizations can leverage proxy servers to filter content for their employees or students. This allows them to restrict access to inappropriate websites or manage internet usage patterns.
- Cost-effectiveness: Compared to dedicated Virtual Private Networks (VPNs), some proxy server options can be a more affordable way to achieve a certain level of privacy or anonymity online.
Also read: What is VPS? | Unveiling the Power Behind Virtual Private Servers
5. Drawbacks of Using a Proxy Server
By understanding the drawbacks of using a proxy server below, you can make an informed decision about whether a proxy server is the right tool for your online needs:
- Limited anonymity: Not all proxies offer complete anonymity. Free or basic proxies might still expose your IP address or browsing activity, especially if they don’t encrypt communication.
- Security risks: Some proxy servers, particularly free ones, might be unreliable or even malicious. They could inject malware into websites you visit or steal your data.
- Performance issues: Proxy servers can add an extra step to your internet connection, potentially slowing down your browsing experience. This depends on the proxy’s location and server load.
- Content blocking: Some websites can detect and block proxy traffic. This might prevent you from accessing the content you were hoping to reach.
- Limited functionality: Proxy servers may not work with all websites or applications. Some services might require a direct connection for optimal functionality.
- Privacy concerns: Even with supposedly anonymous proxies, there’s always a chance the proxy provider itself might log your activity or data.
- Geo-restrictions still apply: While proxies can bypass some geo-restrictions, some streaming services or websites have sophisticated methods to detect and block proxy use.
- Unreliable connections: Free proxies can be overloaded or have unstable connections, leading to frequent disconnects and disruptions.
Also read: What is a Cambodia Server? | Everything You Need to Know
6. Is a Proxy Server Right for You?
Good choice for you if:
It might be the right choice if privacy enhancement is crucial to you, as proxies can conceal your IP address, adding a level of anonymity. They also provide a basic security boost by filtering out malicious content, potentially shielding you from online threats. If you need to access geo-restricted content or websites blocked in your region, proxies can sometimes help bypass these restrictions.
Additionally, organizations find proxies useful for filtering and managing internet access, ensuring compliance with policies and enhancing security for employees or students. These benefits make proxy servers a versatile tool for various privacy, security, and access control needs.
Not ideal for you if:
It might not be the best fit if unwavering anonymity is crucial, especially with free proxies that may not fully anonymize your traffic; a VPN could offer stronger privacy protection. Proxies often lack the encryption capabilities of VPNs, leaving your data vulnerable during transfer if top-notch security is paramount.
They can also introduce additional steps in your internet connection, potentially slowing down your speed, which may not be ideal if speed is essential. If guaranteed access to blocked content is necessary, some advanced websites can detect and block proxy traffic, limiting their effectiveness.
Additionally, proxies may not always support all website functionalities or applications, so consider compatibility when evaluating their suitability for your needs.
7. The Future of Proxy Servers

- With growing concerns over online privacy and data protection, proxy servers will continue to play a crucial role in anonymizing internet traffic and shielding user identities from surveillance and tracking.
- Proxy servers will likely integrate more robust security features, such as improved encryption standards and advanced filtering capabilities, to protect against emerging cyber threats like malware and phishing attacks.
- Organizations will increasingly rely on proxies to enforce stricter access controls, manage internet usage, and ensure compliance with regulatory requirements, particularly in sectors handling sensitive data.
- Advancements in proxy technologies, including AI-driven optimizations, enhanced scalability and better integration with cloud services, will contribute to improved performance and reliability.
- Proxy servers may see greater integration with VPN technologies to offer combined benefits of anonymity and encryption, catering to users’ diverse privacy and security needs.
- Global regulations and restrictions on internet access may drive the demand for proxies as tools to bypass censorship and access geo-blocked content.
8. FAQs
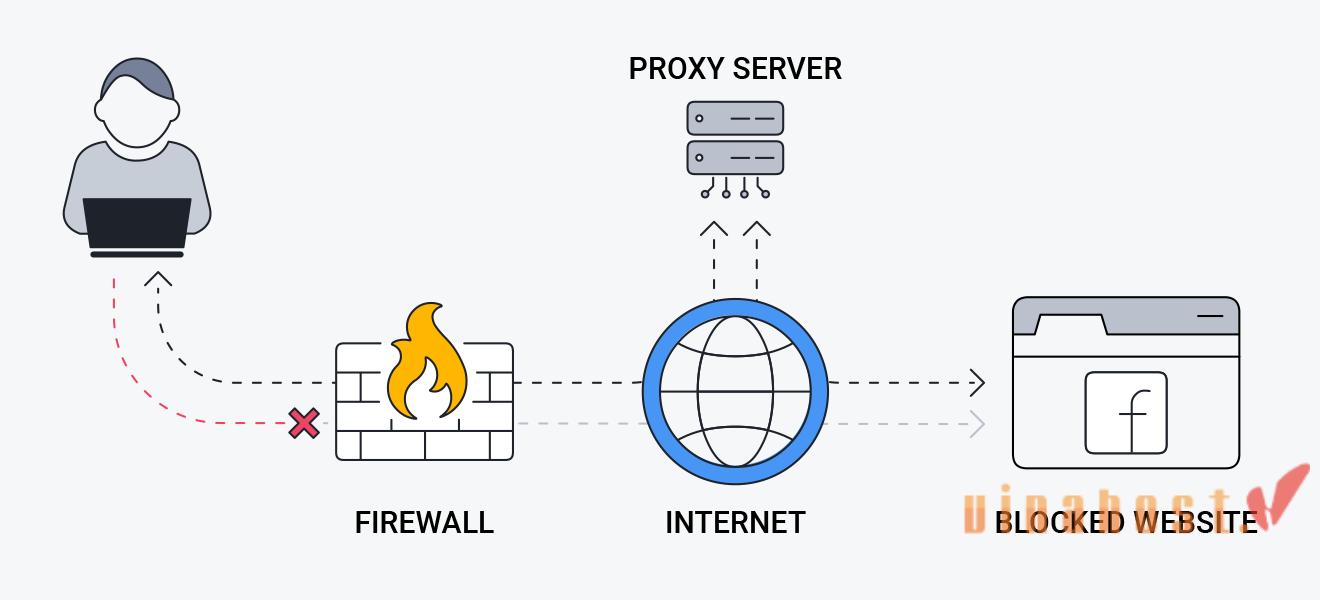
8.1. What is the difference between a Proxy Server and a Firewall?
This table outlines the key differences between a Proxy Server and a Firewall, highlighting their respective functions, capabilities, and typical use cases in network management and security:
| Feature | Proxy Server | Firewall |
| Function | Acts as an intermediary between clients and servers, handling requests on behalf of clients. | Monitors and controls incoming as well as outgoing network traffic based on predefined security rules. |
| Traffic Handling | Routes and filters specific types of traffic, such as web requests, based on configured rules. | Inspects all traffic entering or leaving a network, applying security policies to block or allow traffic. |
| Anonymity | Can provide anonymity by hiding client IP addresses when accessing the internet. | Does not provide anonymity; focuses on controlling traffic flow and enforcing security policies. |
| Content Filtering | Can filter web content based on defined policies, blocking access to specific websites or types of content. | Typically does not perform content filtering; primarily focuses on security policies and traffic control. |
| Encryption | Some proxies, like SSL proxies, can encrypt traffic between clients and servers for secure communication. | May offer VPN capabilities to encrypt traffic, ensuring secure data transfer across networks. |
| Usage | Commonly used for accessing restricted content, enhancing privacy, and managing internet access within organizations. | Essential for network security, protecting against unauthorized access, malware, and data breaches. |
| Location | Positioned between clients and servers on the network perimeter or within internal networks. | Typically deployed at network perimeters to monitor traffic entering and leaving the network. |
8.2. Are proxy servers legal?
Proxy servers themselves are legal to use in many countries and contexts. They serve various legitimate purposes such as enhancing privacy, accessing geo-blocked content, and managing network traffic within organizations.
However, the legality of using a proxy server depends on how you use it and the laws of your specific country. Therefore, before using a proxy server, especially for commercial purposes or in regulated industries, it’s advisable to research and understand the legal implications in your jurisdiction and ensure compliance with applicable laws and regulations.
Here are some things you need to consider before using a proxy server:
- Copyright infringement: Using a proxy server to download copyrighted content illegally is not allowed.
- Cybercrime: Employing a proxy to anonymize yourself while conducting cybercrime is unlawful.
- Violating Terms of Service (TOS): Some websites or services might have terms of service that restrict the use of proxy servers. Make sure you’re not violating any agreements by using a proxy.
- Geographical restrictions: Proxy use to bypass geographical restrictions imposed by content providers or governments may violate local laws or terms of service agreements.
Also read: What is Rack Server? | How does a Rack Server work?
8.3. How much does a proxy server cost?
The cost of a proxy server can vary depending on several factors as follows:
- Type of proxy: Different proxy types like datacenter, residential, or rotating proxies will have different price ranges.
- Level of anonymity: Higher anonymity proxies typically cost more than basic ones.
- Bandwidth: The amount of data you plan to transfer through the proxy will influence the cost.
- Provider: Different proxy service providers will have their own pricing structures.
- Number of IPs: More IP addresses generally mean higher costs.
- Bandwidth: Higher bandwidth limits will increase the price.
- Geolocation: Proxies from specific locations (e.g., certain countries) might be more expensive.
- Support: Premium support services can add to the cost.
- Usage: The volume of data or number of connections can affect pricing.
Here’s a general overview of the costs associated with different types of proxy servers:
Free proxies:
- Cost: $0
- Pros: No cost, easy to find online.
- Cons: Often unreliable, slow, less secure, and can be blocked easily by websites.
Shared proxies:
- Cost: Typically ranges from $5 to $50 per month.
- Pros: More affordable than dedicated proxies.
- Cons: Shared with multiple users, which can affect performance and security.
Dedicated proxies:
- Cost: Usually between $10 and $100 per month.
- Pros: Exclusive use by one user, offering better performance, reliability, and security.
- Cons: Higher cost compared to shared proxies.
Residential proxies:
- Cost: Can range from $10 to $500 per month, depending on usage and provider.
- Pros: Use real residential IP addresses, making them harder to detect and block.
- Cons: More expensive than data center proxies.
Data Center proxies:
- Cost: Generally between $10 and $100 per month.
- Pros: Fast and scalable.
- Cons: Easier to detect and block than residential proxies.
Rotating proxies:
- Cost: Typically from $50 to $500 per month, based on the number of IPs and usage.
- Pros: Frequently changes IP addresses to avoid detection and bans.
- Cons: Can be costly, especially for high-volume usage.
Enterprise solutions:
- Cost: Can range from $500 to several thousand dollars per month.
- Pros: Customized solutions with high security, performance, and support.
- Cons: High cost, suitable for large organizations with specific needs.
8.4. Can proxy servers slow down my internet connection?
Yes, proxy servers can slow down your internet connection. The extent of the slowdown depends on some factors:
- Distance: The further the proxy server is from you geographically, the longer it takes for data to travel back and forth, introducing latency (delay). A proxy server closer to your location will generally offer better speeds.
- Server load: If the proxy server you’re using is overloaded with users, it can become congested and slow down your connection. Opting for a proxy server with a good infrastructure and lower user load can help maintain speed.
- Proxy type: Certain proxy types can add extra steps to the connection process compared to directly accessing a website. For instance, some anonymous proxies might route your traffic through multiple servers, impacting speed.
- Your original Internet speed: If your base internet plan already has slow speeds, using a proxy server might make it feel even slower.
- Encryption Overhead: Proxies that offer encryption, such as SSL proxies, add an extra layer of security but can also introduce additional latency due to the encryption and decryption processes.
To minimize slowdowns when using a proxy server, you can choose a reliable provider known for well-maintained and high-performance proxies. Also opt for proxy servers that are geographically close to your location to reduce latency.
Besides, monitoring your bandwidth usage and selecting a plan that meets your needs can avoid hitting bandwidth limits. Using dedicated or premium proxies also help avoid the slowdowns associated with free or shared proxies.
Finally, ensure your proxy settings are correctly configured for optimal performance, and avoid free proxies, as they are often slower and less reliable compared to paid options.
8.5. Is it difficult to set up a proxy server?

For personal use:
Setting up a proxy server for personal use can be relatively simple, especially if you choose to configure it within your web browser. Modern browsers like Chrome, Firefox, and Safari have built-in settings that allow you to enter the proxy server’s IP address and port number easily.
For instance, in Chrome, you can navigate to Settings, then Advanced, followed by System, and finally Open proxy settings. This method requires minimal technical knowledge and can be completed quickly, making it an accessible option for most users.
Another approach for personal use involves utilizing proxy software such as ProxyCap or Proxifier. These programs allow you to route traffic from specific applications through a proxy server. After installing the software, you enter the proxy server details and select which applications should use the proxy.
This method provides more control over your internet traffic compared to browser-based proxies but is still relatively easy to set up with a moderate level of technical understanding.
For network-wide use:
Configuring a proxy server for network-wide use is more complex and typically involves setting up the proxy on your router or using dedicated proxy server software. Some advanced routers allow you to configure proxy settings directly within their interface.
By accessing your router’s settings through a web browser, you can enter the proxy server details to route all network traffic through the proxy. This method is moderately difficult and requires some knowledge of networking and router configuration, but it can efficiently manage traffic for an entire network.
A more advanced option for network-wide use is installing proxy server software like Squid, Nginx, or HAProxy on a dedicated server within your network. This setup requires downloading and installing the software on a Linux or Windows server, configuring the proxy settings in the software’s configuration files, and ensuring that your devices or router point to this proxy server.
This approach offers extensive customization and control but demands a higher level of technical expertise in server administration and networking, making it suitable for users with advanced skills.
Also Read: What is a Tower Server? | Everything you need to know
9. Conclusion
Through this exploration of what is a proxy server and what does it do, we hope to equip you with the necessary knowledge for proxy server setting.
The difficulty of setting up a proxy server largely depends on your technical knowledge and the complexity of your requirements. Basic proxy configurations, such as those done through web browsers or simple proxy software, are accessible to most users with minimal technical skills. However, more advanced setups for network-wide use require a deeper understanding of networking principles and server management, which can be challenging for less experienced users.
If you need help, don’t hesitate to contact us for support:
- Email: support@vinahost.vn
- Hotline: 1900 6046
- Livechat: https://livechat.vinahost.vn/chat.php
Find out more articles at our Blog or read more:
What is Laos Server? | Everything you need to know
What is a Game Server? | How Game Servers Work?
What is a GPU Server? | Everything you need to know
Maximizing Efficiency and Performance: What is Blade Server?


 Tiếng Việt
Tiếng Việt English
English 简体中文
简体中文