Have you ever wondered what lurks beyond the vibrant screens of your devices? What orchestrates the seamless flow of information and computing experiences you encounter daily? The answer is servers. These devices play a pivotal role in shaping your digital reality, silently orchestrating every click, search, and stream. This article of VinaHost takes you on a journey to find out what is a server, exploring their functions, forms, and their undeniable influence on our modern, interconnected world.
1. What is a Server?
What is server? A server is a computer or system that is dedicated to managing network resources and providing services to other computers, known as clients, within a network. Servers are designed to handle specific tasks or functions, such as storing and managing files, hosting websites, managing network communication, or processing requests for applications and services.
They typically have more processing power, memory, and storage capacity than regular computers to handle the demands of serving multiple clients simultaneously. Servers are an integral part of network infrastructure, facilitating communication, data storage, and the delivery of various services across the internet or within an organization’s internal network.
Also Read: What is a Dedicated Server? | How Does a Dedicated Server Work?
2. Importance of Servers

Servers are the backbone of modern computing infrastructure, supporting a wide range of services and functions critical to businesses, organizations, and individuals. Their reliability, performance, and scalability contribute significantly to the efficiency and functionality of various IT environments.
- Data storage: Servers are used to store and manage large volumes of data. They provide centralized repositories for files, databases, and other critical information, ensuring data accessibility and security.
- Website hosting: Web servers host and serve websites, making them accessible to users over the internet. They handle requests from web browsers, retrieve the necessary data, and deliver web pages to users.
- Application hosting: Servers host various applications and services, enabling users to access software and resources remotely. This is common in cloud computing environments where applications run on servers rather than individual devices.
- Email services: Email servers manage the storage, retrieval, and delivery of emails. They play a vital role in facilitating communication within organizations and globally.
- File sharing: Servers provide a platform for file sharing and collaboration. Users can store, share, and access files from a central location, fostering teamwork and efficient data management.
- Database management: Servers host databases, allowing organizations to store, organize, and retrieve data efficiently. Databases are crucial for applications, analytics, and decision-making processes.
- Network management: Servers oversee network traffic, ensuring efficient communication between devices. They manage protocols, handle security measures, and facilitate the flow of data within a network.
- Backup and recovery: Servers are integral to backup systems, helping organizations create copies of critical data for disaster recovery. They play a crucial role in maintaining data integrity and business continuity.
- Remote access: Servers enable remote access to resources and applications. Users can connect to servers from different locations, fostering flexibility and facilitating remote work.
- Security and authentication: Servers are central to implementing security measures and user authentication. They control access to resources, manage permissions, and enforce security policies to protect data and systems.
Also read: What is Domain & How It Impacts Your Online Presence
3. How Does a Server Work?
In essence, a server acts like a central resource provider on a network, receiving requests from clients, processing them using its hardware and software, and delivering the desired information or functionality in response.
Here is a simplified overview of how a server works. This process is repeated for each incoming request, and servers are designed to handle multiple requests simultaneously, ensuring efficient and timely service delivery.
Request reception:
- A client, which can be a computer, device, or another server, initiates a request by sending a message or signal to the server.
- This request can be for various services like accessing a webpage, retrieving a file, or processing data.
Routing and processing:
- The server’s operating system receives the incoming request and directs it to the appropriate software or application that can fulfill the request.
- The server processes the request, which may involve querying a database, executing a script, or retrieving data from storage.
Data retrieval and processing:
- If the request involves accessing or modifying data, the server interacts with databases or other storage systems to retrieve or update the required information.
- Complex computations or manipulations may be performed based on the nature of the request.
Response generation:
- Once the server processes the request and gathers the necessary data, it generates a response.
- The response typically includes the requested information, such as a webpage, file, or data, along with relevant metadata and status information.
Response transmission:
- The server sends the response back to the client through the network. This can involve using various communication protocols like HTTP for web-based requests or other custom protocols.
Client-side processing:
- The client, upon receiving the response, processes the data and displays it to the user or uses it for further interactions.
- In the case of a web server, the client’s web browser renders the HTML, CSS, and JavaScript to display the requested webpage.
Connection closure (Optional):
- In some cases, the server may close the connection after sending the response. For persistent connections, the server can keep the connection open for multiple requests from the same client.
Logging and monitoring:
- Servers often log information about requests, responses, errors, and other relevant data for monitoring, analysis, and troubleshooting purposes.
Also Read: What is a Nameserver? | A Comprehensive Guide for Beginners
4. Types of Servers
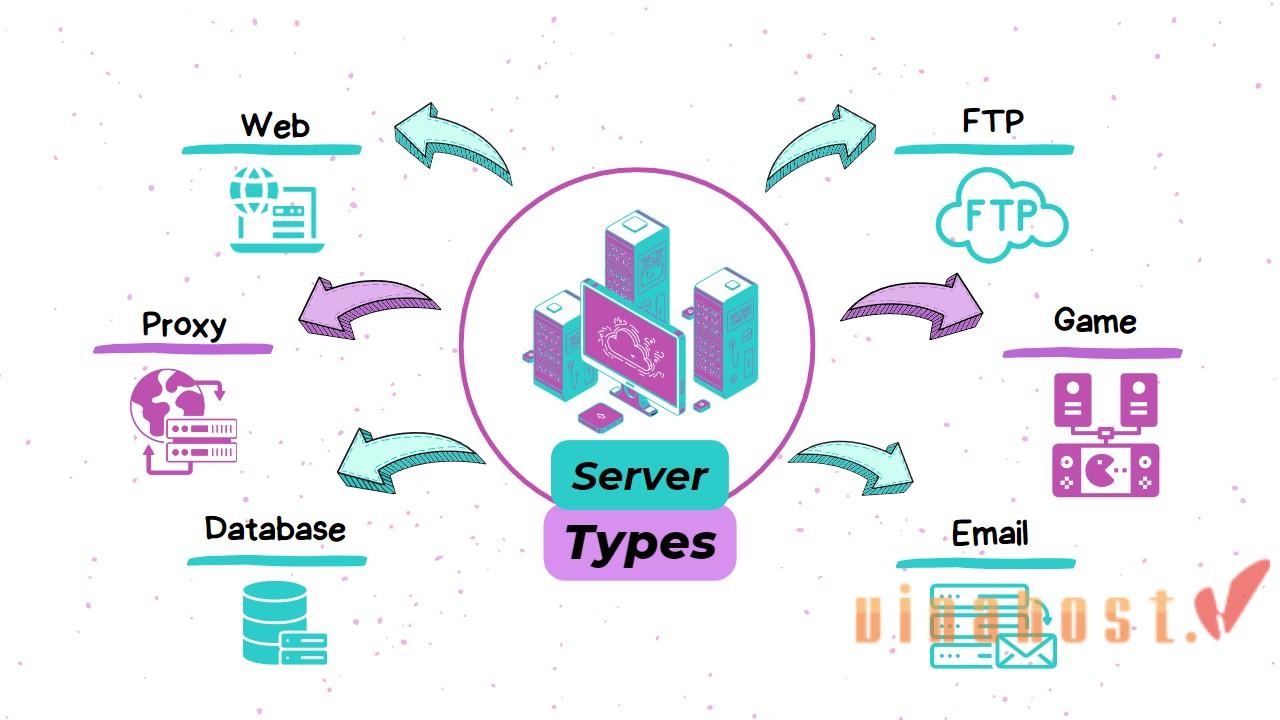
4.1. Web servers
Web servers are responsible for storing, processing, and delivering web pages and content to web browsers when requested. They are the foundation of the World Wide Web and ensure that websites function properly.
Example: Apache HTTP Server, Nginx, Microsoft Internet Information Services (IIS).
4.2. File servers
File servers act as central repositories for storing and managing files. Users on a network can access, share, and collaborate on files stored on the file server. This simplifies data management and ensures centralized backup and security.
Example: Microsoft Windows Server (File Server role), Samba.
4.3. Database servers
Database servers store and manage large amounts of structured data, often used in applications like online transactions, customer records, and product information. They provide efficient storage, retrieval, and manipulation of data for various software applications.
Example: MySQL, Microsoft SQL Server, Oracle Database.
4.4. Application servers
Application servers provide the platform and resources for running web applications and enterprise software. They handle tasks like managing user sessions, security, and communication between the application and databases.
This allows developers to focus on the core functionality of their applications without worrying about the underlying infrastructure.
Example: Apache Tomcat (for Java applications), Microsoft .NET Application Server.
4.5. Print servers
Print servers manage print jobs and resources for a network of computers. Users can send print jobs to the server, which spools them and directs them to the appropriate printer. This eliminates the need for individual computers to have direct connections to each printer.
Example: CUPS (Common Unix Printing System), Windows Print Server.
4.6. DNS servers
DNS (Domain Name System) servers act like phonebooks for the internet, translating human-readable domain names (like [invalid URL removed]) into machine-readable IP addresses.
When you enter a website address in your browser, your computer contacts a DNS server to find the corresponding IP address and route you to the correct website.
Example: BIND (Berkeley Internet Name Domain), Microsoft DNS Server.
Also read: What is DNS Record: The Key to Unlocking the Internet
4.7. Mail servers
Mail servers handle the sending, receiving, storing, and forwarding of email messages. They ensure that emails are delivered to the correct recipients and provide features like email storage and spam filtering.
Example: Microsoft Exchange Server, Postfix, Microsoft Mail.
4.8. Virtual servers
Virtual servers are software-created partitions on a physical server that can act like separate, independent servers. This allows for efficient utilization of hardware resources and enables running multiple servers on a single physical machine.
Example: VMware, Microsoft Hyper-V, VirtualBox.
4.9. Proxy servers
Proxy servers act as intermediaries between clients and the internet. They can filter content, improve security, and cache frequently accessed websites to improve performance.
Example: Squid, Nginx (as a reverse proxy).
Also Read: Maximizing Efficiency and Performance: What is Blade Server?
5. Monitoring and managing servers
Monitoring and managing servers are essential aspects of maintaining a healthy and efficient IT infrastructure.
These practices involve overseeing the performance, availability, and security of servers to ensure optimal operation.
Performance monitoring: Performance monitoring is a critical aspect of server management, involving the continuous tracking of various server resource metrics. This includes monitoring CPU usage, memory consumption, disk space availability, and network activity. Dedicated tools like Nagios or Zabbix provide real-time insights into a server’s performance, enabling administrators to identify bottlenecks, predict potential issues, and optimize resource allocation.
Availability monitoring: Ensuring the availability and responsiveness of servers is fundamental to a reliable IT infrastructure. Availability monitoring involves regularly checking a server’s responsiveness to requests, such as pings or HTTP requests. This practice helps identify downtime or unresponsiveness, allowing administrators to take prompt action to address issues and minimize service interruptions.
Security monitoring: Security monitoring is essential for detecting and responding to potential security threats and vulnerabilities. It involves implementing intrusion detection systems, analyzing server logs for unusual activities, and conducting regular security audits. Security Information and Event Management (SIEM) solutions, such as Splunk, play a crucial role in aggregating and analyzing security-related data to identify and mitigate potential risks.
Log management: Log management is the systematic collection, storage, and analysis of server logs for troubleshooting, security, and compliance purposes. Solutions like the ELK Stack (Elasticsearch, Logstash, Kibana) or Graylog assist in centralizing log data, providing administrators with a comprehensive view of server events for effective troubleshooting and auditing.
Alerting and notification: Effective alerting and notification systems are vital for timely responses to critical events. Configuring alerting rules based on predefined thresholds or abnormal patterns enables administrators to receive notifications when issues arise. Tools such as PagerDuty or Opsgenie help ensure that administrators are promptly informed, allowing for swift action to resolve problems.
Configuration management: Configuration management ensures consistent server configurations and automates deployment processes. Tools like Ansible, Puppet, or Chef facilitate automated provisioning, configuration changes, and version control. This practice enhances efficiency, reduces configuration errors, and streamlines the management of server environments.
Capacity planning: Capacity planning involves anticipating future resource requirements to prevent performance bottlenecks. By analyzing historical performance data, administrators can predict future needs and plan for hardware upgrades or additional resources, ensuring that servers can handle growing workloads effectively.
Patch management: Patch management is crucial for maintaining server security by keeping systems up-to-date with the latest patches and updates. Establishing a systematic approach to applying patches minimizes vulnerabilities and helps protect servers from potential security threats. Dedicated patch management solutions or built-in update mechanisms provided by the server’s operating system assist in this process.
Backup and disaster recovery: Ensuring data integrity and preparedness for unforeseen events is achieved through robust backup and disaster recovery practices. Regularly backing up critical data and testing disaster recovery procedures are essential components of server management. Implementing reliable backup solutions compatible with the server environment is key to quick data recovery in case of server failures or data loss.
Remote server management: Remote server management allows administrators to administer servers from a distance, facilitating troubleshooting and maintenance. This involves implementing secure remote access protocols and using tools like remote desktop solutions or server management platforms such as Microsoft System Center. Remote management enhances flexibility and efficiency in server administration, especially in distributed or cloud-based environments.
Also read: What is HTTPS? The Secure Gateway to a Safer Internet
6. Server Architecture
6.1. Client-server model
The client-server model is a fundamental architecture in computing, where tasks and responsibilities are divided between client devices and server systems. Clients initiate requests for services or resources, and servers respond to these requests, providing the necessary functionalities.
This model facilitates scalability, as multiple clients can connect to a central server or a network of servers. Common examples include web servers handling requests from web browsers and database servers responding to queries from client applications.
The client-server model enables efficient resource utilization, centralized management, and the separation of concerns between client-side and server-side components.
6.2. Server hardware
Server hardware refers to the physical components that make up a server system designed to handle and process network requests. Key elements of server hardware include:
- Processor (CPU): Servers typically feature multi-core processors capable of handling concurrent tasks efficiently.
- Memory (RAM): Servers require ample RAM to store and quickly access data needed for processing requests.
- Storage: Servers use high-capacity and often redundant storage systems for data storage. This can include Hard Disk Drives (HDDs), Solid-State Drives (SSDs), or more advanced storage solutions like Storage Area Networks (SANs).
- Network Interface Cards (NICs): Essential for communication, NICs allow servers to connect to networks, facilitating data exchange with clients and other servers.
- Power supply and redundancy: Servers often incorporate redundant power supplies to ensure continuous operation in case of a power supply failure.
- Cooling systems: Due to the high processing demands, servers include robust cooling systems to prevent overheating.
- Form factor: Servers come in various form factors, such as rack-mounted, tower, or blade servers, depending on the specific use case and infrastructure requirements.
- Redundancy and fault tolerance: Many server setups incorporate redundant components and fault-tolerant configurations to minimize downtime in case of hardware failures.
- Remote management: Advanced server hardware includes features for remote management, allowing administrators to monitor, configure, and troubleshoot servers without physical access.

7. Server Operating Systems
7.1. Windows Server
- Developed by Microsoft, Windows Server is a widely used commercial OS known for its user-friendly interface and compatibility with Microsoft products.
- Popular features include Active Directory for centralized user management, Hyper-V for server virtualization, and robust security features.
- Commonly used for: Active Directory integration, file and print services, web hosting, and general-purpose server applications.
7.2. Linux Server
- A free and open-source operating system known for its stability, security, and customization options.
- Popular distributions include Red Hat Enterprise Linux (RHEL), Ubuntu Server, and CentOS (though future development is uncertain).
- Offers a wide range of server applications and is often preferred for its flexibility and cost-effectiveness for specific needs.
- Commonly used for: Web hosting, email servers, database servers, and cloud computing deployments.
7.3. Unix Server
- A family of multi-user operating systems known for their reliability, security, and command-line interface.
- Popular variants include Solaris, AIX, and HP-UX (usage has declined in recent years).
- Often used in mission-critical environments like financial institutions and high-performance computing due to their stability and security features.
Also read: What is VPS? | Unveiling the Power Behind Virtual Private Servers
8. Server Functions
8.1. File storage and sharing
One of the primary functions of servers is to provide centralized file storage and sharing capabilities. Servers act as repositories for data, documents, and files accessible to users within a network.
This function is crucial for maintaining data consistency, security, and accessibility. File servers facilitate collaborative work by allowing users to store, retrieve, and share files seamlessly. Network Attached Storage (NAS) and Storage Area Networks (SAN) are common server configurations for efficient file storage and sharing.
8.2. Data backup and recovery
Servers play a vital role in data backup and recovery processes to safeguard against data loss and ensure business continuity. Regular backups of critical data are stored on servers, often in redundant configurations or offsite locations.
This practice protects against accidental deletion, hardware failures, or other unforeseen events. In case of data loss, servers facilitate the recovery process by restoring data from backup copies. Backup servers and dedicated backup software contribute to creating comprehensive and reliable data protection strategies.
8.3. Hosting websites and applications
Servers are essential for hosting websites and applications, providing the necessary infrastructure for them to be accessible over the internet or within a local network. Web servers handle incoming requests from clients (web browsers) and deliver the requested web pages.
Application servers execute and manage software applications, serving dynamic content to users. Servers hosting websites and applications can range from simple setups for small businesses to complex configurations, including load balancers, content delivery networks (CDNs), and database servers for handling high traffic volumes.
9. Server Security
9.1. Importance of server security

Server security is of paramount importance in maintaining the integrity, confidentiality, and availability of data and services within an organization.
Safeguarding sensitive data:
Servers are prime targets for hackers seeking to steal sensitive information like customer details, financial data, and intellectual property. A successful breach can lead to:
- Financial losses: Companies may face hefty fines and settlements for data breaches, depending on regulations and the nature of the data exposed.
- Reputational damage: A data breach can significantly damage an organization’s reputation, leading to a loss of customer trust and loyalty.
- Legal consequences: Depending on the severity of the breach and the data involved, legal repercussions can arise.
Maintaining business continuity:
Cyberattacks can disrupt or disable critical services hosted on the server, causing:
- Operational downtime: This can translate to lost productivity, revenue, and customer satisfaction.
- Damage to brand reputation: Downtime can negatively impact an organization’s image and customer trust.
- Financial losses: Downtime can lead to lost revenue, especially for e-commerce businesses and those relying on online services.
Preventing malware and ransomware attacks:
Malware infections: Malicious software can infect servers, compromising their functionality, corrupting data, and spreading to other devices on the network. This can result in:
- Data loss and corruption: Malware can destroy or alter important data, hindering operations and causing financial losses.
- System performance degradation: Malware can slow down server performance, impacting user experience and productivity.
- Increased security risks: A compromised server can become a launchpad for further attacks within the network.
Ransomware attacks: This specific type of malware encrypts data, rendering it inaccessible, and demands a ransom payment to restore access. This can lead to:
- Significant financial losses: Ransomware attacks can cripple businesses, forcing them to pay hefty ransom demands or face the potential loss of critical data.
- Disruption of operations: Encrypting essential data can render systems and applications unusable, halting operations and causing significant disruption.
9.2. Common security measures
- Firewalls: Firewalls act as a barrier between a server and potential threats, controlling incoming and outgoing network traffic based on predetermined security rules.
- Access controls: Implementing strict access controls ensures that only authorized personnel have access to critical server resources. This includes user authentication, authorization, and least privilege principles.
- Encryption: Encrypting data in transit and at rest adds an extra layer of protection. Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols secure communication over networks, while encryption algorithms protect stored data.
- Regular patching and updates: Keeping server software, operating systems, and applications up-to-date is crucial for addressing known vulnerabilities. Regular patching helps eliminate security loopholes that could be exploited by attackers.
- Intrusion detection and prevention systems (IDPS): IDPS monitors network or system activities, identifies suspicious patterns, and takes preventive actions to stop potential threats.
- Security audits and monitoring: Regular security audits and monitoring help detect anomalies, unauthorized access, or potential security incidents. Log analysis and real-time monitoring tools contribute to the early detection of security threats.
- Backup and disaster recovery: Regular backups of critical data ensure that in the event of a security incident or data loss, organizations can recover essential information. A well-defined disaster recovery plan helps minimize downtime.
- Antivirus and antimalware software: Deploying robust antivirus and antimalware solutions helps detect and remove malicious software, reducing the risk of infections and compromises.
- User education and training: Human factors play a significant role in security. Educating users about security best practices, social engineering threats, and the importance of strong passwords enhances the overall security posture.
- Physical security: Physical security measures, such as access controls, surveillance, and secure server room environments, prevent unauthorized physical access to servers.
Also read: What is a Top-Level domain? | Everything You Need to Know TLDs
10. Server Maintenance
Just like any complex machine, servers require regular maintenance to ensure they function optimally, efficiently, and securely. This preventive care helps to:
- Minimize downtime and disruptions: By proactively addressing potential issues, you can avoid unexpected failures and maintain service availability.
- Improve performance and efficiency: Regular maintenance can optimize server resource utilization, leading to faster processing speeds and better response times.
- Enhance security: Applying updates and patches promptly addresses vulnerabilities and strengthens your defenses against cyber threats.
10.1. Regular updates and patches
Software updates: Install the latest updates for your server operating system and applications as soon as they become available. These updates often include:
- Bug fixes: Addressing known software bugs and ensuring smooth operation.
- Security patches: Plugging security vulnerabilities to prevent cyberattacks and data breaches.
- New features and enhancements: Implementing improved functionalities and performance optimizations.
Scheduled updates: Automate updates whenever possible to streamline the process and ensure timely application.
Testing updates: In critical environments, consider testing updates in a non-production environment before deploying them to live servers to minimize the risk of unexpected disruptions.
10.2. Performance monitoring
- Continuously monitor server performance: Track key metrics such as CPU usage, memory utilization, disk space, and network traffic.
- Identify potential problems: Analyze the collected data to identify potential bottlenecks, resource constraints, or unusual activity that could indicate impending issues.
- Set up alerts: Configure alerts to be notified when specific metrics fall outside predefined thresholds, allowing for prompt intervention and troubleshooting.
- Performance optimization: Based on monitoring data, implement measures to optimize server performance, such as resource allocation adjustments or hardware upgrades.
11. Server Management Tools
11.1. Remote server management tools
- SSH (Secure Shell): SSH is a widely used protocol for secure remote server management. It allows administrators to access the command-line interface of a server remotely, facilitating configuration, troubleshooting, and system maintenance.
- Remote Desktop Protocol (RDP): RDP is a proprietary protocol developed by Microsoft for remote desktop access to Windows servers. It provides a graphical user interface for administrators to manage servers remotely.
- Web-based control panels: Various web-based control panels, such as cPanel, Plesk, and Webmin, offer intuitive interfaces for server management. These tools enable administrators to perform tasks like configuring domains, managing databases, and setting up email accounts through a web browser.
- Ansible: Ansible is an open-source automation tool that allows administrators to define and manage server configurations as code. It simplifies tasks such as software installation, configuration updates, and system provisioning across multiple servers.
11.2. Server monitoring software
- Nagios: Nagios is a popular open-source monitoring system that provides real-time monitoring and alerting for servers, network devices, and applications. It offers a centralized dashboard and customizable alerts to notify administrators of potential issues.
- Zabbix: Zabbix is an open-source monitoring solution that provides comprehensive monitoring capabilities, including performance metrics, event correlation, and visualization. It supports various notification methods and offers a web-based interface for configuration and reporting.
- Prometheus: Prometheus is an open-source monitoring and alerting toolkit designed for reliability and scalability. It focuses on time-series data collection, making it suitable for tracking server performance metrics over time.
- SolarWinds Server & Application Monitor (SAM): SAM is a commercial server monitoring tool that offers real-time performance monitoring, automated alerting, and customizable dashboards. It provides insights into server health, application performance, and infrastructure dependencies.
- Datadog: Datadog is a cloud-based monitoring and analytics platform that offers server monitoring, log management, and application performance monitoring. It provides a unified view of server metrics, logs, and traces for comprehensive analysis.
- New relic: New Relic is a cloud-based observability platform that includes server monitoring, application performance monitoring (APM), and infrastructure monitoring. It provides insights into server performance and dependencies in a dynamic environment.
- PRTG Network Monitor: PRTG is a network monitoring solution that also offers server monitoring capabilities. It provides customizable dashboards, real-time alerts, and historical data analysis for servers and network devices.
12. Future of Servers

Edge computing:
- Decentralized Processing: Edge computing’s focus on processing data closer to its source, reducing latency, and supporting real-time applications aligns with the increasing demand for quicker and more efficient data processing.
Containerization and microservices:
- Efficient Resource Utilization: Containerization and microservices promote agility, scalability, and efficient resource utilization. This trend is central to modern application development and deployment practices.
Serverless computing:
- Event-Driven Architecture: Serverless computing’s event-driven model, where developers focus on writing functions without managing servers, offers enhanced scalability, cost-effectiveness, and streamlined development processes.
AI and machine learning integration:
- Smart Resource Management: The integration of AI and machine learning into server management enhances proactive maintenance, performance optimization, and intelligent resource allocation, contributing to overall efficiency.
Hybrid cloud and Multi-cloud adoption:
- Flexibility and Scalability: The adoption of hybrid cloud and multi-cloud strategies provides organizations with flexibility, scalability, and the ability to choose the most suitable environment for various workloads, reflecting the dynamic nature of modern IT infrastructure.
13. FAQs
13.1. Can I use a personal computer as a server?
Yes, you can use a personal computer as a server for certain purposes, such as hosting a home server, file server, or development server. The feasibility depends on the computer’s hardware specifications, operating system, intended use, network capabilities, and security considerations.
Personal computers may be suitable for less resource-intensive tasks, but for demanding applications like hosting large-scale websites or critical business services, dedicated server hardware or cloud-based solutions with higher performance specifications and reliability are often more appropriate.
Additionally, ensure your personal computer can handle continuous 24/7 operation, and implement proper security measures and backup solutions if exposing the server to the internet.
13.2. Are servers only used by large businesses?
No, servers are not exclusive to large businesses; they are utilized by a diverse range of entities, including small businesses, individuals, and organizations of varying sizes. While large enterprises often employ powerful and complex server infrastructures to support extensive IT needs, small businesses and individuals can leverage servers for specific purposes like file storage, website hosting, or running applications.
The advent of cloud computing has also democratized access to server resources, allowing businesses of all sizes to benefit from scalable and cost-effective server solutions. Whether managing data, hosting websites, or supporting collaborative projects, servers play a crucial role in enhancing efficiency and connectivity across the spectrum of business and personal computing needs.
13.3. How often should I update the server software?
The frequency of updating server software depends on various factors, including the type of server, the software in use, and the criticality of the applications or data it manages. Generally, it is advisable to stay proactive with updates to enhance security, performance, and reliability.
Security updates should be applied promptly, as they often address vulnerabilities and protect against potential threats. For more stable and established server environments, routine maintenance windows, such as monthly or quarterly, may be suitable.
However, critical security patches should be applied as soon as they become available. Always follow best practices for testing updates in a controlled environment before applying them to a production server to avoid potential disruptions. Additionally, keeping an eye on software vendor recommendations and industry security alerts helps ensure timely and informed updates.
13.4. Can I run multiple types of servers on a single machine?
Yes, it is possible to run multiple types of servers on a single machine. This is often achieved through virtualization or containerization technologies. Virtualization allows you to create virtual machines (VMs) on a single physical server, each running its own operating system and hosting different types of servers.
Containerization, on the other hand, enables the isolation of applications and their dependencies into lightweight containers, allowing multiple containers, each running a specific server type, to coexist on the same host machine. This approach enhances resource efficiency and flexibility, enabling you to run diverse server types simultaneously on a single server.
13.5. What is the difference between a server and a cloud server?
The main difference between a traditional server and a cloud server lies in their infrastructure and deployment model.
| Traditional Server | Cloud Server | |
| Infrastructure | A traditional server refers to a physical server that is a tangible piece of hardware, often located on-premises within an organization’s data center. | A cloud server, or virtual server, is part of a cloud computing infrastructure and operates in a virtualized environment. It is not a physical machine but rather a virtual instance running on shared physical hardware. |
| Ownership and Maintenance | Organizations own and maintain traditional servers, including handling hardware upgrades, maintenance, and security measures. | Cloud servers are provided by cloud service providers (e.g., AWS, Azure, Google Cloud). The provider manages the underlying infrastructure, including hardware maintenance, upgrades, and security. |
| Scalability | Scaling resources on traditional servers may involve physical upgrades, which can be time-consuming and may require additional hardware. | Cloud servers offer easy scalability. Resources can be quickly scaled up or down based on demand, and users pay for the resources they consume on a pay-as-you-go model. |
While traditional servers are physical machines owned and managed by the organization, cloud servers operate in a virtualized environment provided by a third-party cloud service provider. The cloud server model offers greater flexibility, scalability, and reduced operational overhead compared to traditional servers.
VinaHost – Your Partner for Server in Vietnam
We’ve just reviewed the diverse types of servers, from web and application servers to specialized database and email servers, recognizing that each fulfills a unique, vital role in your IT infrastructure. Choosing the correct server type—or combination of types—is a crucial decision that directly impacts your performance, security, and operational efficiency. You need robust, flexible, and scalable hardware to support your specific server functions.
At VinaHost, we don’t just offer generic hosting; we provide the Server Vietnam and colocation solutions specifically tailored to house and operate whatever server type your business requires. Whether you need a high-speed bare metal server optimized for a demanding Application Server or a secure, stable environment for a critical Database Server, our services deliver unmetered bandwidth, redundant power, and 24/7/365 professional monitoring. Our diverse hardware portfolio ensures we can configure the ideal physical foundation for your chosen server type.
Conclusion
In a digital realm where speed, efficiency, and accessibility are paramount, the significance of web servers cannot be overstated. They stand as the silent guardians, responding to our queries, delivering web pages, and ensuring the fluidity of our online interactions. Whether you’re a web developer, a business owner, or an avid user of the internet, this dual exploration has equipped you with insights into the machinery that powers the online world.
Read more:


 Tiếng Việt
Tiếng Việt English
English 简体中文
简体中文