SSH stands for Secure Shell, which is the leading solution for remote access between two computers with high security. So what is SSH? What are its advantages? How do you use it? The following article from VinaHost will provide you with extremely detailed and useful information for those who are new to SSH.
1. What is SSH?
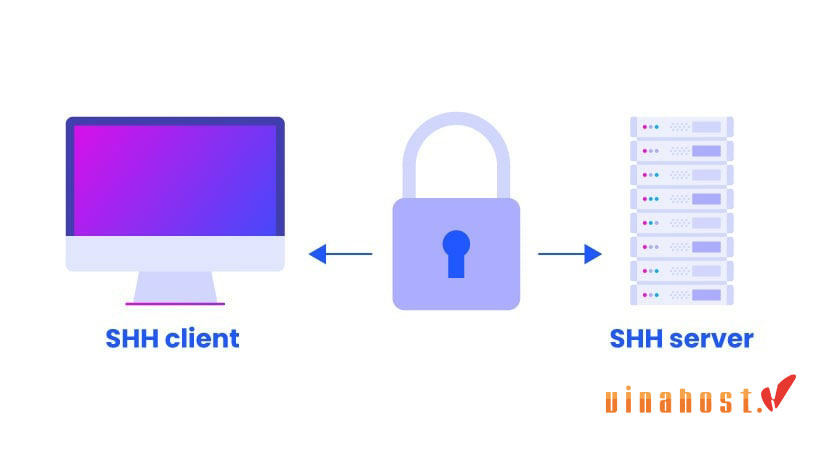
SSH stands for Secure Shell. It is a cryptographic network protocol that allows secure communication and data transfer over unsecured networks.
It provides a secure channel over an insecure network by encrypting the data during transmission. It is commonly used for remote login and command execution on remote computers or servers. It replaces insecure protocols like Telnet and FTP, providing better security and protection against eavesdropping and other attacks.

Also Read: What is HTTPS? The Secure Gateway to a Safer Internet
2. The History of SSH
SSH was initially developed in 1995 by Tatu Ylönen, a researcher at Helsinki University of Technology. Later on, Ylönen founded SSH Communications Security, a cybersecurity company located in Finland. As time passed, several vulnerabilities were discovered in SSH-1, rendering it obsolete and insecure for contemporary use.
In 2006, SSH-2, the latest iteration of Secure Shell protocols, was officially recognized as a Standards Track specification by the Internet Engineering Task Force (IETF). Unlike SSH-1, SSH-2 operates independently and implements a more robust security mechanism, employing a Diffie-Hellman key exchange and enhanced integrity verification through message authentication codes.
Among the encryption techniques available for SSH clients and servers, the most prevalent are Advanced Encryption Standard (AES) and Blowfish. While SSH-2 currently has no documented exploitable vulnerabilities, revelations from Edward Snowden in 2013 implied that the National Security Agency (NSA) might possess capabilities to decrypt certain traffic.
3. The Role of SSH
It plays a crucial role in facilitating secure remote access and data transfer between computers or servers over unsecured networks. It ensures confidentiality, integrity, and authenticity of the communication by encrypting the data transmitted between the client and the server.
By providing a secure channel for remote login and command execution, it effectively mitigates risks associated with eavesdropping, tampering, and unauthorized access. Additionally, SSH protocols have evolved over time to address security vulnerabilities, with SSH-2 being the current standard recognized by the Internet Engineering Task Force (IETF).
Despite occasional concerns about potential decryption capabilities by certain entities, it remains an indispensable tool for securely managing and administering remote systems and networks.
Overall, SSH plays a critical role in ensuring the security, efficiency, and reliability of remote access, system administration, and file transfer operations in diverse computing environments. Its robust encryption, authentication, and communication capabilities make it an indispensable tool for secure communication and remote management in both personal and enterprise settings.
Also Read: Unveiling the Web’s Hidden Foundation: What is Web Hosting?
4. How Does SSH Work?
The operation of SSH involves three main stages as follows:
Stage 1: Encryption
In this stage, it employs both symmetric encryption and asymmetric encryption to secure the transmission of information.
- Symmetric encryption: It uses a single key for both encryption and decryption of data. This key is shared between the client and the server.
- Asymmetric encryption: It utilizes two keys, a public key and a private key. The public key is shared with everyone, while the private key is kept secure.
Stage 2: Authentication
In the second stage of the connection process, the client uses the server’s public key to generate a session key. This session key will be used to encrypt all communication between the client and the server throughout the connection session.
Stage 3: Server Authentication
It employs server authentication methods to ensure that users are connecting to a trusted server.
When a client connects to a server, the server sends an authentication message to the client. This message contains the server’s name and a public key. The client uses this public key to verify the identity of the server.
Throughout this process, SSH employs cryptographic techniques such as asymmetric encryption, symmetric encryption, hash functions, and digital signatures to ensure confidentiality, integrity, and authenticity of the communication between the client and server. This robust security framework makes SSH a trusted protocol for secure remote access and data transfer.
Read more: Price of Servers in Vietnam
5. What is SSH used for?
Included as a default feature in Unix, Linux, and Mac servers, SSH is a standard component across all data centers. SSH connections serve to secure a wide array of communications between a local machine and a remote host, encompassing secure remote access to resources, command execution remotely, software patch delivery, updates, and various administrative or management tasks.
Aside from establishing a secure connection between local and remote computers, it is employed for the administration of routers, server hardware, virtualization platforms, operating systems (OSes), and internal system management and file transfer applications.
Secure Shell serves as a means to connect to servers, enact modifications, conduct uploads, and terminate sessions, either through dedicated tools or directly via the terminal. SSH keys are utilized to automate server access and frequently find applications in scripts, backup systems, and configuration management tools.
Engineered for ease of use and compatibility across organizational structures, SSH keys offer single sign-on (SSO) capabilities, enabling users to navigate between their accounts seamlessly without the need to input a password repeatedly.
Beyond its authentication functionality over encrypted connections, it plays vital roles in identity and access management. All traffic is encrypted, ensuring user privacy whether they are transferring files, browsing the web, or executing commands.
Although it can utilize conventional user IDs and passwords for authentication, it predominantly relies on public key pairs to authenticate hosts to one another. While individual users still need to use their user ID and password (or alternative authentication methods) to connect to the remote host directly, the local and remote machines authenticate independently of each other.
This is achieved by generating a distinct public key pair for each host involved in the communication. For a single session, two public key pairs are required: one pair to authenticate the remote machine to the local machine and another pair to authenticate the local machine to the remote machine.
Also Read: What is a Server? Understanding the Backbone of Modern Technology
6. Benefits of SSH
6.1. Enhanced Security
One of the primary benefits of SSH is its strong encryption capabilities, which ensure that data transmitted between the client and server is secure and cannot be intercepted easily by malicious actors. It uses various cryptographic algorithms to protect the integrity and confidentiality of data.
6.2. Versatility and Flexibility
It can be used for various purposes such as remote login, file transfer, and command execution, making it a versatile tool for managing remote systems.
6.3. Efficient Resource Utilization
It optimizes resource usage by allowing multiple tasks to be performed over a single secure connection, reducing overhead and improving efficiency.
6.4. Strong Authentication Mechanisms
SSH provides various methods for authenticating users, including passwords, public key authentication, and multi-factor authentication. This helps ensure that only authorized users can access the system or server remotely.
6.5. Port Forwarding and Tunneling
SSH supports port forwarding, allowing users to securely tunnel connections between local and remote ports. This feature enables secure access to services running on remote machines that would otherwise be inaccessible due to firewall restrictions or network configurations.
6.6. Data Integrity
SSH verifies the integrity of data transmitted over the network using cryptographic hash functions. This ensures that data remains unchanged during transmission and guards against tampering or manipulation by unauthorized parties.
6.7. Remote Access
SSH enables users to remotely access and manage systems or servers securely over an untrusted network, such as the internet. This is particularly useful for system administrators, developers, and remote workers who need to access resources located on remote machines.
6.8. File Transfer
SSH includes utilities like SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol) for securely transferring files between computers. These tools leverage SSH’s encryption and authentication mechanisms to ensure the confidentiality and integrity of transferred data.
6.9. Platform Independence
SSH is platform-independent, meaning it can be used on various operating systems, including Linux, macOS, and Windows. This flexibility makes it a widely adopted solution for secure remote access and data transfer across different environments.
7. Difference between SSH and Telnet
Although both are protocols used for remote connections, SSH (Secure Shell) and Telnet have several differences. Let’s explore through the following comparison:
Security
- SSH: Provides high security with data encryption and strong authentication.
- Telnet: Lacks similar security measures, data is not encrypted and susceptible to interception.
Authentication
- SSH: You can use passwords or public-private key pairs for identity verification.
- Telnet: Only uses passwords, offering lower security.
Data Transmission
- SSH: Ensures secure data transmission with information encryption, preventing eavesdropping and tampering.
- Telnet: Transmits data in plain text, not encrypted, susceptible to interception or alteration.
Usage
- SSH: Typically used for remote management and accessing servers remotely.
- Telnet: Used for remote connection and control, but does not ensure high security.
8. Difference between SSH and SSL/TLS
SSH (Secure Shell) and SSL/TLS (Secure Sockets Layer/Transport Layer Security) are both cryptographic protocols designed to provide secure communication over networks, but they serve different purposes and have distinct features. Let’s examine the differences between them:
Purpose
- SSH: Primarily used for secure remote login, command execution, and data transfer between two computers or servers.
- SSL/TLS: Designed for securing network communication between a client and a server, commonly used in web browsers for secure browsing (HTTPS), email servers, VPNs, and other applications that require secure data transmission over the internet.
Layer
- SSH: Operates at the application layer (Layer 7) of the OSI model.
- SSL/TLS: Operates at the transport layer (Layer 4) or sometimes at the session layer (Layer 5) of the OSI model.
Encryption
- SSH: Uses symmetric encryption, asymmetric encryption, and key exchange algorithms to encrypt data and authenticate users.
- SSL/TLS: Utilizes symmetric encryption, asymmetric encryption, and digital certificates for secure data transmission and server authentication.
Authentication
- SSH: Supports various authentication methods, including passwords, public-key cryptography, and multi-factor authentication.
- SSL/TLS: Relies heavily on digital certificates issued by trusted certificate authorities (CAs) to authenticate servers and, optionally, clients.
Applications
- SSH: Mainly used for secure remote administration, file transfer, and tunneling purposes.
- SSL/TLS: Widely employed for securing web browsing, email communication, VPN connections, and any other application requiring secure data transmission over the internet.
Port
- SSH: Typically operates on port 22 by default.
- SSL/TLS: Typically operates on port 443 for HTTPS, but can also use other ports depending on the application.
Connection Type
- SSH: Provides point-to-point connections between a client and a server.
- SSL/TLS: Supports both point-to-point connections and connections between a client and multiple servers (e.g., in the case of load balancing or CDN).
While SSH and SSL/TLS both offer encryption and authentication for secure communication, they are designed for different purposes and operate at different layers of the OSI model. SSH is primarily used for remote administration and data transfer between machines, while SSL/TLS is commonly used for securing internet communication between clients and servers.

9. Future of SSH
The future of Secure Shell looks promising, with ongoing efforts aimed at enhancing its security, efficiency, and usability. Here are some potential directions in the future:
- Security Enhancements: As cyber threats evolve, there will be continuous efforts to improve security. This may include implementing stronger cryptographic algorithms, enhancing key management systems, and mitigating emerging threats such as quantum computing.
- Multi-Factor Authentication (MFA): Integrating MFA into authentication processes can provide an extra layer of security, making it harder for unauthorized users to gain access even if they obtain valid credentials.
- Simplification and Usability Improvements: While it is a powerful tool, its complexity can be a barrier to entry for some users. Future developments may focus on making more user-friendly through better documentation, intuitive interfaces, and automation features.
- Performance Optimization: Efforts to optimize performance will continue, especially for use cases where low-latency communication is crucial, such as remote administration of high-performance computing clusters or real-time data transfer.
- Containerization and Cloud Integration: With the increasing adoption of containerization and cloud computing, there will be a growing demand for integration with container orchestration platforms (e.g., Kubernetes) and cloud management services (e.g., AWS, Azure, Google Cloud).
- Standardization and Interoperability: Standardization efforts will likely continue to ensure interoperability between different implementations and compatibility with various operating systems and network environments.
- Open Source Community Contributions: The open-source nature of SSH means that its development relies heavily on community contributions. Future innovations will likely come from the collaborative efforts of developers around the world, addressing both security concerns and user needs.
- Integration with Next-Generation Technologies: As technologies like artificial intelligence (AI), machine learning (ML), and the Internet of Things (IoT) become more prevalent, SSH may evolve to better integrate with these technologies, enabling secure communication and management in diverse environments.
Overall, while it has been a cornerstone of secure remote communication for decades, its evolution will continue to adapt to emerging technologies and security challenges, ensuring its relevance in the future digital landscape.
Also Read: What is Domain & How It Impacts Your Online Presence
10. FAQs
10.1. Can SSH be used for file transfers?
Yes, it can indeed be used for file transfers. One of the most common tools for file transfer over SSH is “scp” (secure copy). “scp” allows you to securely transfer files between a local and a remote host or between two remote hosts. It encrypts both the file contents and the commands used to transfer the files, providing a secure method for transferring sensitive data over a network.
Here’s a basic usage example of “scp”:
scp /path/to/local/file username@remotehost:/path/to/destination
This command copies a file from the local system to a remote system. You replace “/path/to/local/file” with the path to the file on your local system, “username” with your username on the remote host, “remotehost” with the hostname or IP address of the remote system, and “/path/to/destination” with the path where you want to copy the file on the remote system.
Similarly, you can also copy files from a remote host to your local system:
scp username@remotehost:/path/to/remote/file /path/to/destination
In addition to “scp”, there are other methods for file transfer over SSH, such as using SFTP (SSH File Transfer Protocol) or using SSHFS (SSH File System) to mount remote directories locally. Each method has its own advantages and use cases, but they all leverage SSH’s encryption and authentication mechanisms to ensure secure file transfers.
10.2. Is SSH only used for remote access to servers?
While it is most commonly known for providing secure remote access to servers, its usage extends beyond remote server administration. Here are some additional ways is used:
- Secure File Transfer: As mentioned earlier, it is commonly used for secure file transfer using tools like “scp”, SFTP (SSH File Transfer Protocol), or SSHFS (SSH File System). These methods encrypt the data during transmission, ensuring confidentiality and integrity.
- Tunneling and Port Forwarding: It can create encrypted tunnels between a local and a remote host, allowing secure communication over untrusted networks. This feature is often used for accessing services behind firewalls, securely connecting to databases, or accessing intranet resources from outside the network.
- Remote Command Execution: It allows users to execute commands on remote systems securely. This functionality is not limited to server administration but can also be used for automation, batch processing, or running remote scripts.
- Git and Version Control: Git, a popular version control system, can use SSH for secure communication between repositories and clients. Keys are commonly used for authentication in Git repositories hosted on platforms like GitHub, GitLab, and Bitbucket.
- Secure Communication for IoT Devices: It can be used to establish secure communication channels between IoT devices and servers, ensuring data confidentiality and integrity in IoT deployments.
- Secure Shell Proxy: It can act as a proxy server, allowing users to securely browse the internet or access restricted content through an encrypted tunnel.
- Secure Remote Desktop Access: While less common than other methods, it can also be used for remote desktop access, especially in conjunction with other tools or protocols like X11 forwarding or VNC (Virtual Network Computing).
These are just a few examples of how SSH is utilized beyond remote server access. Its versatility, security features, and wide availability make it a valuable tool for various network-related tasks in both professional and personal settings.
10.3. Is SSH compatible with IPv6?
Yes, it is compatible with IPv6. IPv6 support has been integrated into SSH implementations for quite some time now. Both the client and server components can work seamlessly over IPv6 networks, allowing secure communication between IPv6-enabled hosts.
When connecting to a remote host using SSH over IPv6, the syntax is the same as when connecting over IPv4. You simply specify the IPv6 address of the remote host instead of an IPv4 address.
For example, to connect to a remote host over using its IPv6 address:
ssh username@[IPv6_address]
Replace [IPv6_address] with the actual IPv6 address of the remote host, and “username” with your username on that host.
Similarly, if you’re running an server on an IPv6-enabled host, clients connecting to it over IPv6 can do so using the standard SSH client commands.
SSH’s compatibility with IPv6 ensures that it can be used seamlessly in modern networking environments where IPv6 adoption is increasing.

Also read: What is IPv6? | Understanding the Future of Internet Addressing
10.4. Is SSH difficult to use?
It can seem daunting at first, especially for those who are not familiar with command-line interfaces or networking concepts. However, once you become acquainted with its basic usage, it is relatively straightforward to use. Here are some factors to consider regarding the difficulty:
- Command Line Interface: It is primarily used through the command line, which can be intimidating for beginners who are accustomed to graphical user interfaces (GUIs). However, many SSH clients provide graphical interfaces as well, making it more accessible to users who prefer point-and-click interactions.
- Authentication and Key Management: Understanding SSH authentication methods, such as password-based authentication and public key authentication, may require some initial learning. Managing SSH keys, especially for public key authentication, can also be perceived as complex by some users. However, once set up, SSH keys provide a more secure and convenient way to authenticate.
- Syntax and Options: It commands may involve various options and parameters, which can be overwhelming for newcomers. However, most common usage scenarios involve only a few basic commands and options, such as connecting to a remote host (ssh) or transferring files (scp). Learning these basic commands can greatly simplify the use.
- Security Considerations: It is designed with security in mind, and it’s essential to follow best practices to ensure secure usage. This includes configuring SSH securely, managing SSH keys properly, and keeping SSH software up to date. While these considerations are important, they may add complexity to the initial setup and configuration.
- Documentation and Resources: There are extensive resources available online, including tutorials, guides, and documentation, to help users learn and troubleshoot usage. Utilizing these resources can make the learning process smoother and reduce the perceived difficulty of using it
While it may initially appear challenging due to its command-line interface and security considerations, it becomes more manageable with practice and familiarity. Additionally, graphical interfaces and abundant documentation resources can help simplify the learning curve for new users.
10.5. Is SSH secure?
Secure Shell is generally considered a secure protocol for remote access and communication between computers. It provides encryption and authentication mechanisms to ensure secure communication over an insecure network. However, like any technology, its security depends on proper configuration and usage.
Here are some reasons why it is considered secure:
- Encryption: It encrypts all data transmitted between the client and server, including passwords, commands, and output. This prevents eavesdropping by malicious parties.
- Authentication: It supports various authentication methods, including passwords, public key cryptography, and multi-factor authentication (MFA). Strong authentication mechanisms help ensure that only authorized users can access the system.
- Integrity: It includes mechanisms to ensure the integrity of data transmitted between the client and server. This helps detect if data has been tampered with during transmission.
- Port Forwarding: It allows secure port forwarding, which can be used to encrypt other network traffic, such as web browsing or database connections.
- Key Management: Keys can be generated and managed securely, allowing for robust authentication without the need for passwords.
However, despite these security features, it can still be vulnerable if not configured and used correctly. Common vulnerabilities include weak passwords, outdated software versions, misconfigured settings, and compromised private keys.
To maximize security when using SSH, it’s important to:
- Use strong passwords or, preferably, keys for authentication.
- Keep software and system software up to date with security patches.
- Disable protocol versions that are known to be insecure.
- Limit access to services through firewalls and access controls.
- Monitor logs for suspicious activity.
By following best practices and regularly reviewing and updating security measures, SSH can be an effective and secure tool for remote access and communication.
10.6. What are some alternatives to SSH?
Several alternatives to SSH exist, each with its own features and use cases. Here are a few:
- TLS/SSL VPN (Virtual Private Network): TLS or SSL VPNs provide secure remote access to networks by creating an encrypted tunnel between the client and the network. This allows users to access network resources securely as if they were physically connected to the network.
- WireGuard: WireGuard is a modern VPN protocol known for its simplicity and performance. It aims to be faster and more efficient than traditional VPN protocols like OpenVPN or IPSec.
- OpenVPN: OpenVPN is an open-source VPN solution that uses SSL/TLS for key exchange and encryption. It’s widely used for creating secure point-to-point or site-to-site connections.
- ZeroTier: ZeroTier is a lightweight, peer-to-peer VPN alternative that creates virtual networks with secure communication between devices. It’s easy to set up and suitable for various use cases, including remote access and network segmentation.
- Teleport: Teleport is an open-source SSH alternative designed for modern infrastructure environments. It provides secure access to servers, Kubernetes clusters, and other resources, along with audit trails and session recording.
- Mosh (Mobile Shell): Mosh is a remote terminal application that provides continuous connectivity even when the client’s IP address changes or the connection is interrupted. It’s particularly useful for mobile and roaming users.
- Guacamole: Apache Guacamole is a clientless remote desktop gateway that allows users to access their desktop environments through a web browser. It supports various protocols, including VNC, RDP, and SSH.
These alternatives offer different features and capabilities, so the choice depends on factors such as security requirements, ease of use, scalability, and specific use cases.
11. Conclusion
The article from Vinahost has provided you with a comprehensive overview of what SSH is. Hopefully, with the valuable information provided, it will help you develop and operate your website effectively.
Find out more service:
What is a Dedicated Server? | How Does a Dedicated Server Work?
What is Colocation? | How does Colocation work?
What is VPS? | Unveiling the Power Behind Virtual Private Servers


 Tiếng Việt
Tiếng Việt English
English 简体中文
简体中文